Start CCS
- After installation, CCS will automatically start up when the endpoint boots.
- The real-time virus monitor is enabled by default, so endpoints are protected immediately after the restart.
- Important - We recommend admins configure CCS via an Endpoint Manager profile rather than locally.
- Log into 'Endpoint Manager' > Click 'Configuration Templates' > 'Profiles' > open a Mac OS profile > Click the 'Antivirus' tab.
- However, you can also configure the application at a local machine should you wish. The rest of this guide addresses how to use the application locally.
You can access the management interface in the following ways:
Launchpad- Open the launchpad on your Mac device
- Click the Comodo Client Security icon to open the application
The taskbar (top-right) lets you open the application, enable/disable real-time scanning, switch to silent mode, and manage your CCS configurations.
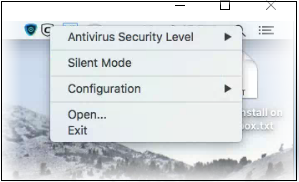
- Antivirus Security Level – Enable or disable the real-time virus monitor:
- On Access - Any file opened is scanned before it is allowed to run.
- Disabled - Switches the real-time scanner off.
- Silent Mode - Temporarily disable alerts so they don't interrupt you when running a full screen presentation or playing a game. Protection remains enabled.
- Configuration - Create, import and export CIS security configurations. This is useful if you want to implement specific settings on multiple endpoints.
- Open... - Open the CCS main interface.
- Click 'Open' to launch the application
- Use the quick launch icon on the MAC OS dock to open the interface at any time:

|
Tip: You can scan a file or folder by simply dragging it onto the CCS dock icon. If the icon is not present, you can add it as follows:
|
The summary screen opens:
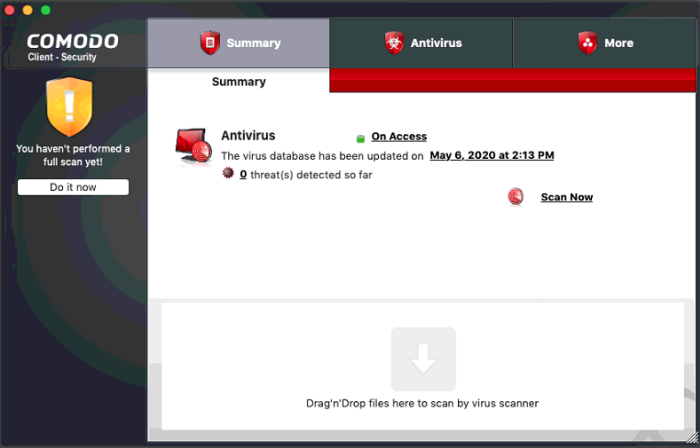
- Click 'Do it now' to run your first full computer scan.
Before running the scan, CCS will first check for AV database updates. If updates are available they will be downloaded and installed.
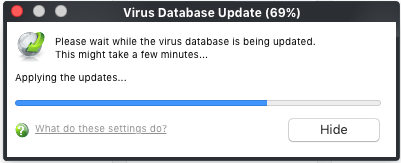
The scan will commence after the update:
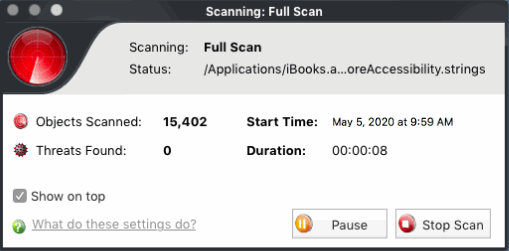
Scan results are shown at the end of the scan.
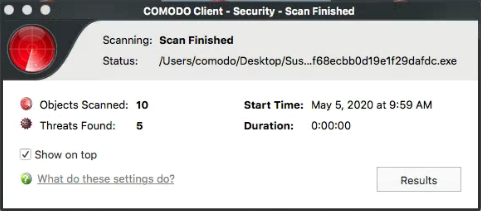
- The results window lists all threats discovered by the scan. You can remove selected threats or choose to ignore them:
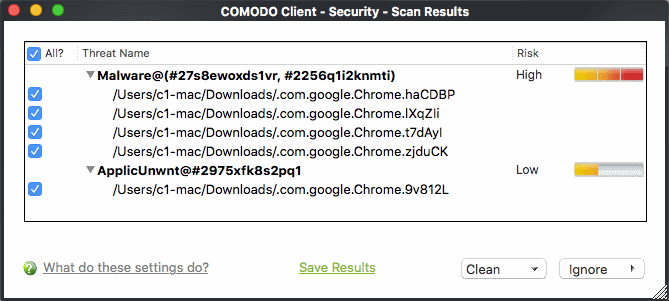
See Scan and Clean Your Computer for more details.


