Export Certificate for use on Endpoint Manager and Tigase Server
Export Certificate from Windows to .pfx format:
Step 1 - View certificate information using mmc.exe
- Note: Asure you have installed a certificate onto your machine where
- Right-click the 'Start' > 'Run'
- Type mmc.exe > hit 'Enter'
From 'Console Root'
- Click 'File' then 'Add' / 'Remove Snapin…'
- Select the 'Certificates' from the list and click 'Add'
If you are not sure whether or not the certificate is under a user or a computer account, add them both
- Click 'OK' to load the interface
- Browse the certificate you want to use (usually is under the 'Personal' > 'Certificates' folder

- Double-click the certificate name to open to view its detailed information
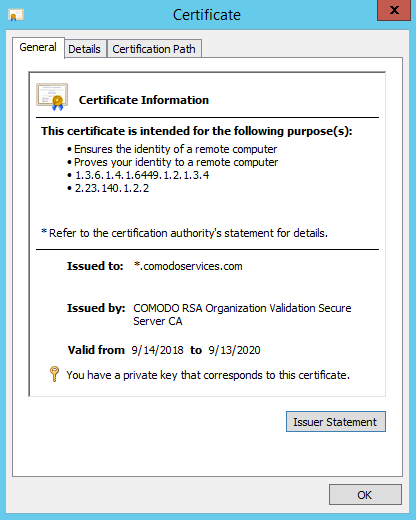
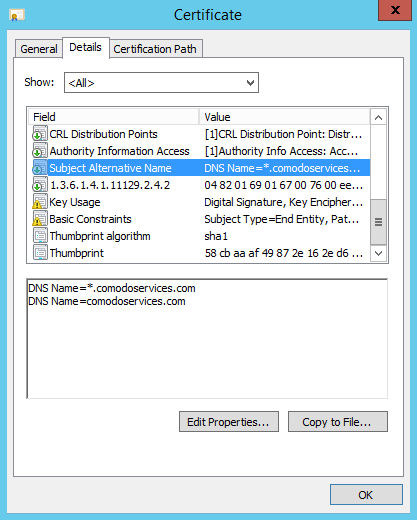
- 'General' tab - view the certificate private key associated with it and validate the certificate, anything.comodoservices
- You will not be able to validate comodoservices.com
- 'Details' tab > select 'Subject Alternative Name' section to confirm the validation
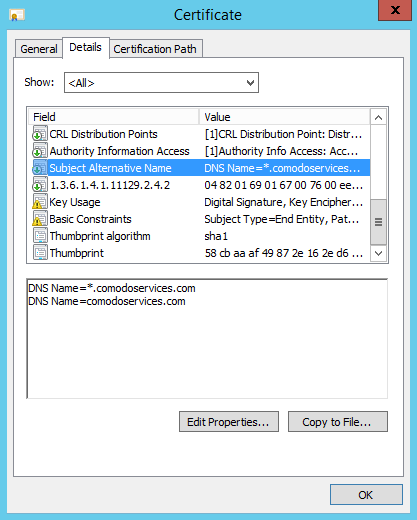
- There are two entries:
- The first entry - validate anything.comodoservices.com
- The second entry - validate the main domain comodoservices.com
- If you are using a multidomain certificate, you can see all the FQDN’s/IP’s that the certificate is able to cover. In our case this wildcard certificate will suit our needs
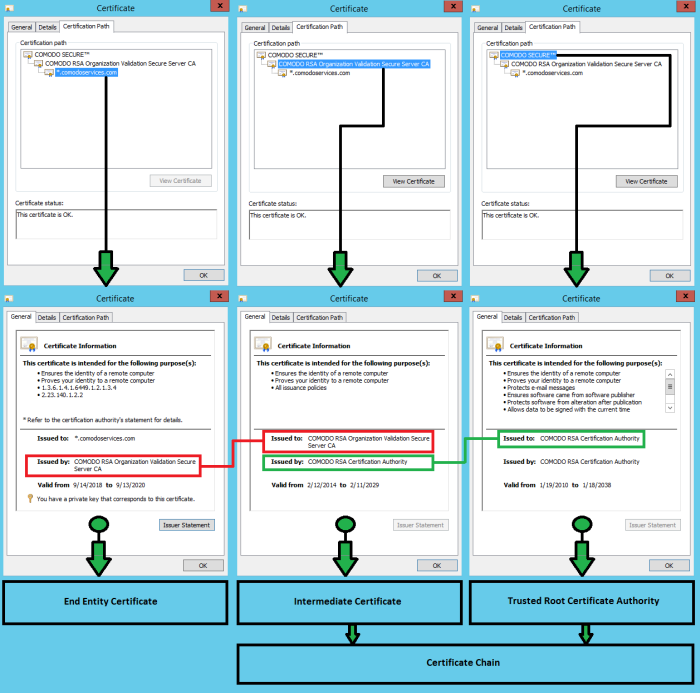
- 'Certificate Path' tab - view the certificate chain and confirm that the End Entity Certificate is able to link to a trusted root certificate using one or two intermediate certificates.
- In our example, one intermediate certificate:
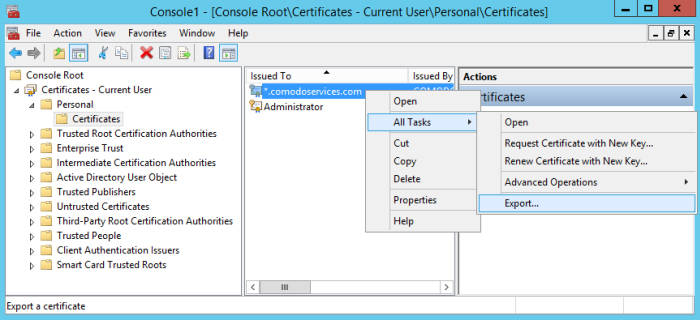
Step 2: Export the certificate to .pfx format
From the 'Certificates' window
- Right-click the certificate name > 'All Tasks' > 'Export…'
- Click Next

- Please select “Yes, export the private key” > click 'Next'
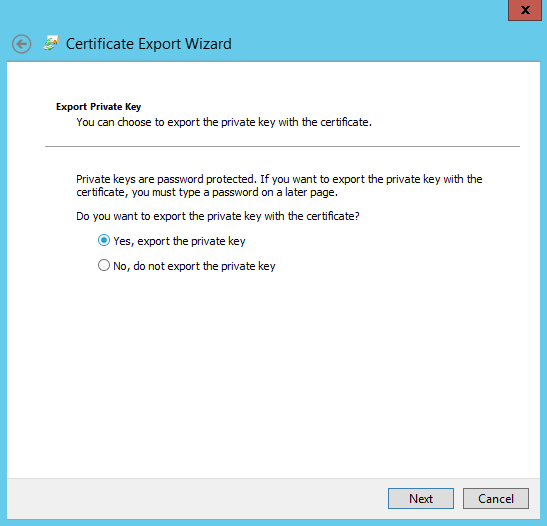
- Select “Include all certificates in the certification path if possible” > click 'Next' to include the certificate chain
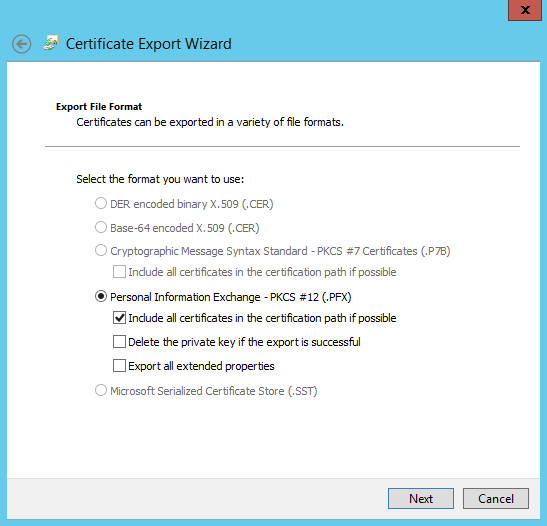
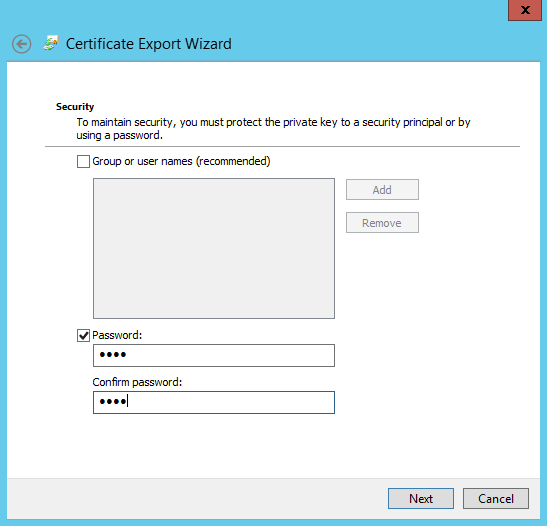
- Provide a password > click 'Next'
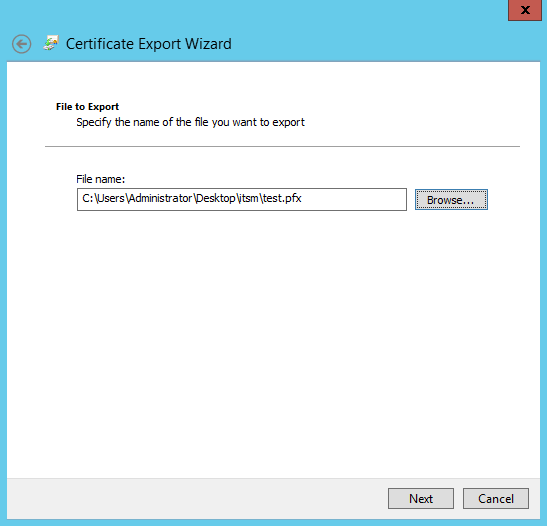
- Specify a name, select place to save it > click 'Next'
- The last step, click 'Finish' to export the certificate to a .pfx file
Options to prepare Endpoint Manager (ITSM) server and Tigase certificates using openssl
It has 2 options to extract certificates to use them in the Endpoint Manager (ITSM) server and Tigase server:
2. Option 2: Manually create cert.crt, cert.key and comodoservices.com.pem from a .pfx file
Option 1: Use the script scriptpfx.sh to create cert.crt, cert.key and in this case comodoservices.com.pem
- Create a folder on the itsm or tigase server using for example FileZilla
- Copy the .pfx file to the folder
- Create
file
scriptpfx.shin the created folder (near .pfx file) with following content:
#!/bin/bashopenssl pkcs12 -in $1 -nocerts -nodes -passin pass:$2 | sed -ne '/-BEGIN PRIVATE
KEY-/,/-END PRIVATE KEY-/p' > clientcert.key
openssl pkcs12 -in $1 -clcerts -nokeys -passin pass:$2 | sed -ne '/-BEGIN
CERTIFICATE-/,/-END CERTIFICATE-/p' > clientcert.crt
openssl pkcs12 -in $1 -cacerts -nokeys -chain -passin pass:$2 | sed -ne '/-BEGIN
CERTIFICATE-/,/-END CERTIFICATE-/p' > cacerts.crt
a="$(openssl crl2pkcs7 -nocrl -certfile cacerts.crt | openssl pkcs7 -print_certs -text -noout | sed -n 's/^.*CN=//p' | sed -n 1p)"
b="$(openssl crl2pkcs7 -nocrl -certfile cacerts.crt | openssl pkcs7 -print_certs -text -noout | sed -n 's/^.*CN=//p' | sed -n 2p)"
if [ "$a" == "$b" ]; then
cabundle="$(cat cacerts.crt | wc -l)"
if [ "$cabundle" -gt 1 ]; then
cat cacerts.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END
CERTIFICATE-/p; /-END CERTIFICATE-/q' > rootca.crt
cat cacerts.crt > intermediatefile.crt
nr="$(cat rootca.crt | wc -l)"
sed -i 1,"${nr}"d intermediatefile.crt
cat rootca.crt > newcertificatechain.crt
cabundle1="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END
CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate1.crt
cat intermediate1.crt >> newcertificatechain.crt
nr1="$(cat intermediate1.crt | wc -l)"
sed -i 1,"${nr1}"d intermediatefile.crt
cabundle2="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN
CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate2.crt
cat intermediate2.crt intermediate1.crt rootca.crt >
newcertificatechain.crt
rm intermediate2.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
else
cat intermediate1.crt rootca.crt >
newcertificatechain.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
fi
else
cat rootca.crt > newcertificatechain.crt
rm rootca.crt
rm intermediatefile.crtfi
cat clientcert.key > cert.key
cat clientcert.crt newcertificatechain.crt > cert.crt
cat clientcert.key clientcert.crt newcertificatechain.crt > $3
rm clientcert.key
rm clientcert.crt
rm cacerts.crt
rm newcertificatechain.crt
else
echo The certificate chain is not included in the $1.
echo Please create again the $1 and include the certificate chain.
fi
else
cat clientcert.key > cert.key
cat clientcert.crt newcertificatechain.crt > cert.crt
cat clientcert.key clientcert.crt cacerts.crt > $3
rm clientcert.key
rm clientcert.crtrm cacerts.crt
fi
-
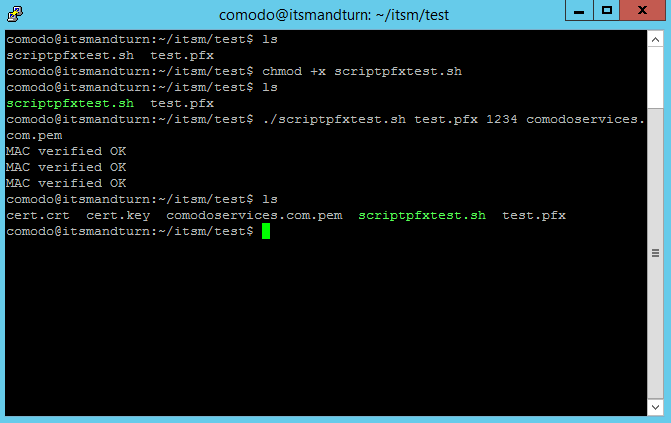
Run
chmod +x scriptpfxtest.shto make the file executable -
Run
./scriptpfxtest.sh test.pfx 1234 comodoservices.com.pemto generate cert.crt, cert.key and comodoservices.com.pemFormat to use the command:
./scriptpfxtest.sh Parameter1 Parameter2 Parameter3
Where:
- Parameter1: test.pfx – is the name of the .pfx file
- Parameter2: 1234 – is the password for the .pfx file
- Parameter3: comodoservices.com.pem – is the FQDN.pem that you want to use
The script execution will create:
- cert.key
- cert.crt
- comodoservices.com.pem
To confirm that files are generated correctly, use the following commands:
openssl
crl2pkcs7 -nocrl -certfile cert.crt | openssl pkcs7 -print_certs
-text -noout | sed -n 's/^.*CN=//p'
This confirms whether the certificate chain is in the correct order from top to bottom:
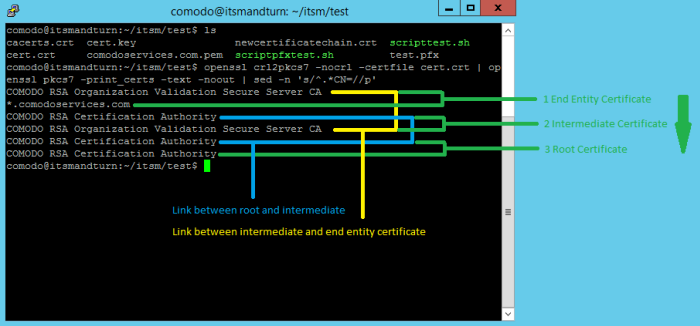
You can use the same command on the Tigase certificate. Example: comodoservices.com.pem.
The difference between Endpoint Manager (ITSM) and Tigase certificates is that the Tigase certificate has a private key on top.
To verify this, we can use the following command:
cat
comodoservices.com.pem | sed -n 1p
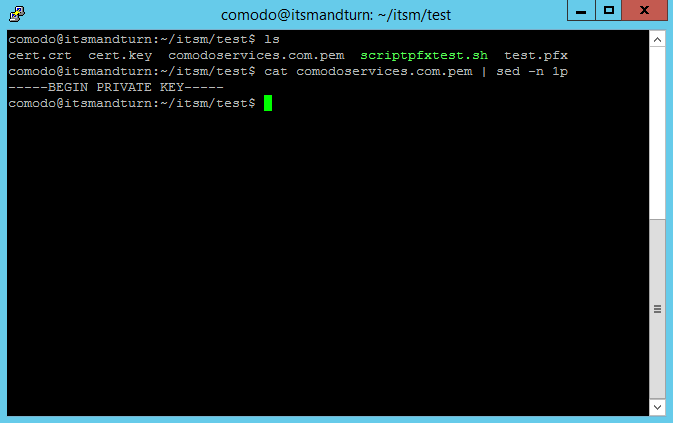
- Verify
the private key using the command:
openssl
rsa -in cert.key -check

Use the following command to confirm that the private key is associated with the certificate :
openssl
x509 -noout -modulus -in cert.crt | openssl md5openssl rsa
-noout -modulus -in cert.key | openssl md5
You will receive the same number on confirmation that private key is associated with the certificate.
Option 2: Manually create
cert.crt, cert.key and comodoservices.com.pem from a .pfx file
- Copy the .pfx file on a folder on Endpoint Manager (ITSM) or Tigase server using for example FileZilla
Run this command to create cert.key:
openssl
pkcs12 -in test.pfx -nocerts -nodes | sed -ne '/-BEGIN PRIVATE
KEY-/,/-END PRIVATE KEY-/p' > cert.key
To extract only the certificate, run the command:
openssl
pkcs12 -in test.pfx -clcerts -nokeys | sed -ne '/-BEGIN
CERTIFICATE-/,/-END CERTIFICATE-/p' > clientcert.crt
- To extract the certificate chain, run the command:
openssl
pkcs12 -in test.pfx -cacerts -nokeys -chain | sed -ne '/-BEGIN
CERTIFICATE-/,/-END CERTIFICATE-/p' > cacerts.crt
- To confirm the cacerts.crt has the correct order, run the command:
openssl
crl2pkcs7 -nocrl -certfile cacerts.crt | openssl pkcs7 -print_certs
-text -noout | sed -n 's/^.*CN=//p'
If
the certificate chain is as order, bottom to top instead of top to
bottom, you can use script to reverse the order.
- Create
file
scriptorder.sh(in the folder near .pfx file) with following content:
#!/bin/bash
cabundle="$(cat $1 | wc -l)"
if [ "$cabundle" -gt 1 ]; then
cat $1 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END
CERTIFICATE-/q' > rootca.crt
cat $1 > intermediatefile.crt
nr="$(cat rootca.crt | wc -l)"
sed -i 1,"${nr}"d intermediatefile.crt
cat rootca.crt > newcertificatechain.crt
cabundle1="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END
CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate1.crt
cat intermediate1.crt >> newcertificatechain.crt
nr1="$(cat intermediate1.crt | wc -l)"
sed -i 1,"${nr1}"d intermediatefile.crt
cabundle2="$(cat intermediatefile.crt | wc -l)"
if [ "$cabundle1" -gt 1 ]; then
cat intermediatefile.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p; /-END CERTIFICATE-/q' > intermediate2.crt
cat intermediate2.crt intermediate1.crt rootca.crt >
newcertificatechain.crt
rm intermediate2.crt
rm intermediate1.crt
rm rootca.crt
rm intermediatefile.crt
else
cat intermediate1.crt rootca.crt > newcertificatechain.crt
rm intermediate1.crt
rm rootca.crtrm intermediatefile.crtfielsecat rootca.crt >
newcertificatechain.crt
rm rootca.crt
rm intermediatefile.crt
fi
else
echo The file is empty.
echo Lines = $cabundlefi
-
Run the script. To make the script executable use the command:
chmod +x scriptorder.sh -
Once the script is executable, run it by providing the cacerts.crt as parameter:
./scriptorder.sh cacerts.crt
See example below:
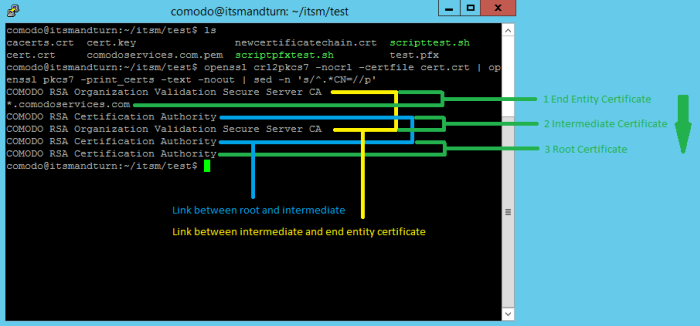
If you don’t want to use the script, use the following commands to extract certificates in order:
- This command will extract the first certificate from the file, in our case the root:
cat
cacerts.crt | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p;
/-END CERTIFICATE-/q' > rootca.crt
-
The second command deletes the certificate from the cacerts.crt to be able to extract the second available certificate
nr="$(cat
rootca.crt | wc -l)";sed -i 1,"${nr}"d cacerts.crt
Use these three commands to
extract your certificate chain and use cat to concatenate them in the correct order.
-
Example to create comodoservices.com.pem:
cat
cert.key clientcert.crt intermediate.crt root.crt >
comodoservices.com.pem
-
Example to create cert.crt:
cat
clientcert.crt intermediate.crt root.crt > cert.crt
Use options from Option 1 to verify them and confirm that the certificate files have been created/extracted correctly.


