Antivirus Logs
Antivirus logs contain statistics on all discovered threats. This includes the time of the event, the malware name, and the action that taken on the threat.

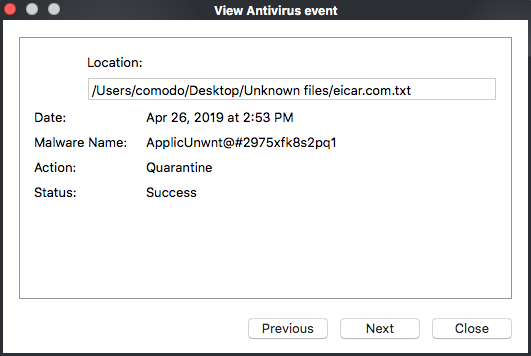
1. Date - The time of the event.
2. Location - The path where the threat was found.
3. Malware Name - Malware label.
4. Action - Action taken on the malware. This can be 'Quarantine', 'Detect' or Ignore'.
5. Status – States whether the attempted action succeeded or failed.
6. Scan UID - The unique identification code of the scan profile that caught the malware. Each profile has its own UID. All zeroes = code for a real-time scan.
Double-click on an entry to view a summary of the log:
You can right-click on an item to view further options:
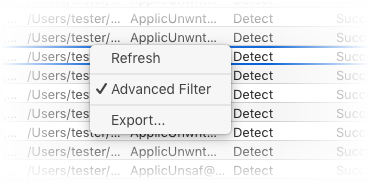
- Refresh – Adds recently created logs to the list
- Advanced Filter – Filter AV events by various criteria, including action, type and more
- Export... - Save the events list as an HTML file


