Filter Antivirus Logs
You can create custom views of all logged events according to the following criteria:
- Action - Filter events according to the response (action taken) by the antivirus
- Location - Filter events by the path at which the malware was found
- Malware Name - Display only those events that reference a specific piece of malware
- Status - Filter events according to whether the attempted action was successful or not. Status options are 'Success' or 'Fail'
Configure Event Filters
- Open Comodo Client Security
- Click 'More' > 'View Antivirus Events'
- Click the 'More' button to open the log viewer module
- Right-click inside the log viewer module and select 'Advanced Filter'
OR
- Click 'View' on the menu bar and select 'Advanced Filter'
- Select a filter criteria and click 'Add'
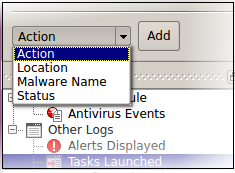
1. Action: Filter logs by the response to the threat. You can then select a specific action. For example, only show events where the threat was quarantined.
- Select 'Equal' or 'Not Equal' from the drop-down.
- Equal – Show only events which feature the action you select. You can select multiple actions.
- Not Equal - Inverts your choice. For example, select 'Not Equal' + 'Ignore' to view every event except those that were ignored.
- Choose the events you want to view:
- Quarantine: Events where the threat was placed in quarantine
- Remove: Events where the user chose to delete a threat
- Ignore: Events where the user allowed the threat to proceed
- Detect: Events where a piece of malware was first identified
- Ask: Events where the user was asked to provide a response to a discovered threat. Users are asked for their response at an alert, or the results screen at the end of a scan. The response from the user might be 'Quarantine', 'Remove', 'Ignore' or 'Restore'.
- Restore: Events where the user removed the threat from quarantine and moved it back to its original location.
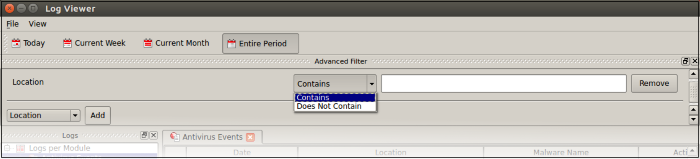
2. Location: View logs that concern files at a specific path. You need to enter the path in the field provided:

- Select 'Contains' or 'Does Not Contain' from the second drop-down:
- Contains - Show only events which concern items at the location you specify. You can add multiple locations
- Does Not Contain – Inverts your choice. Show all events except those at the location you specify
3. Malware Name: Filter logs by the label of the malicious item. You need to enter the name of the malware in the field provided:
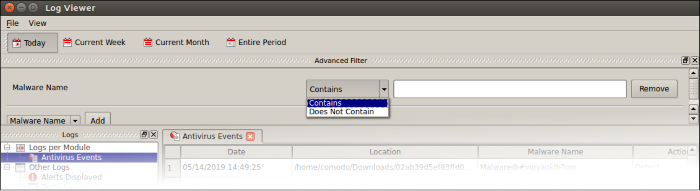
- Select 'Contains' or 'Does Not Contain' from the second drop-down:
- Contains – Show only events which concern the malware named in the text field. You can add multiple malware names.
- Does Not Contain – Inverts your choice. Show all events except those that involve the malware you specify.
4. Status: Filter logs by whether or not the action taken on the threat was successful. You can view only successful actions, or only failed actions.
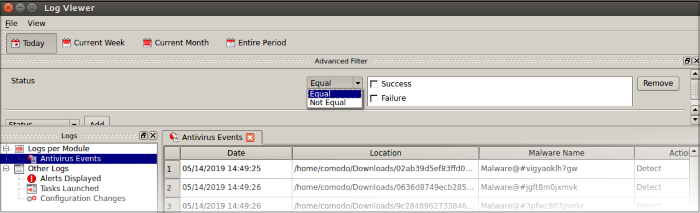
- Select 'Equal' or 'Not Equal' from the drop-down.
- Equal – Show only events which feature the result you select.
- Not Equal - Inverts your choice. For example, select 'Not Equal' + 'Success' to view every event except those that were successful.
- Choose the outcomes you want to view:
- Success: View events where the task in the 'Action' column was completed.
- Failure: View events where the task in the 'Action' column was not completed.


