Tool Set
- Click 'Tools' on the menu bar.
The tools area contains a suite of free productivity and security applications. Each tool is designed to help customers accomplish specific management and security tasks more efficiently.
Download ITarian tools
- Click 'Tools' on the menu bar
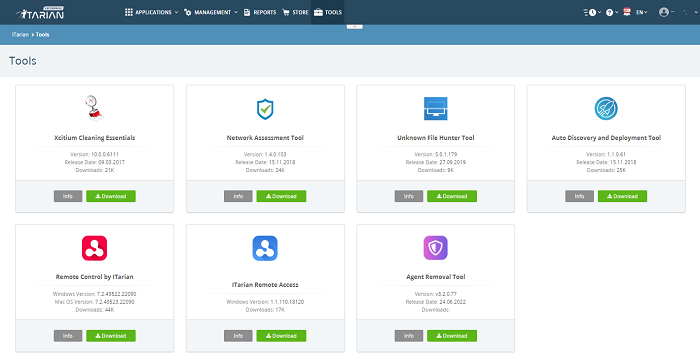
The following are available:
- Xcitium Cleaning Essentials - Security
software for Windows which removes malware and kills unsafe
processes on infected computers. Includes a fully customizable
malware scanner and a tool which lets you identify
and terminate unsafe
processes with a single click. See 'Xcitium Cleaning Essentials' for more information.
- Network
Assessment Tool – Scan
customer networks to identify a wide range of server, endpoint and
network vulnerabilities. The tool also generates detailed reports
and risk mitigation plans with actionable advice to address each
issue. See 'Network
Assessment Tool' to find out more.
-
Unknown File Hunter Tool - Unknown file hunter (UFH) is a lightweight scanner that identifies unknown and potentially malicious files residing on networks. Scanned files are categorized as 'safe', 'malicious' or 'unknown'. Unknown files are those that were not found on either the safe-list or the blacklist and could potentially contain zero-day threats. The UFH scanner allows you to upload such files to our Valkyrie servers where they will undergo a battery of run-time tests designed to reveal whether or not they are harmful. You can view the results of these tests in the UFH interface. See 'Unknown File Hunter Tool' to find out more.
- Auto Discovery and Deployment Tool - Remotely deploy applications to multiple endpoints via Active Directory, Workgroup or IP address/IP range/host name. See 'Auto Discovery and Deployment Tool' to find out more.
- Remote Control by ITarian - Remotely access Windows and Mac OS devices to solve issues, install third party software or run system maintenance. See 'Remote Control by ITarian' to find out more.
- ITarian Remote Access Tool – Independent tool for system administrators to view and address issues instantly. See ITarian Remote Access Tool to know more details.
- Agent Removal Tool - Delete any files and registry keys that may remain on a Windows endpoint after a regular uninstall of Agents. See Agent Removal Tool for more details.
Network Assessment Tool
- Scan customer networks to identify all vulnerabilities and threats.
- Detailed client risk report assigns a score to each threat found on an endpoint.
- Risk mitigation plans contain advice to address every discovered issue.
- Easy setup lets you import networks via Active Directory, Workgroup or IP range.
Download NAT
- Click 'Tools' in the top-menu
- Locate the Network Assessment Tool' tile
- Click the 'Download' button.
- Select
the operating system of the server on which you wish to install NAT.
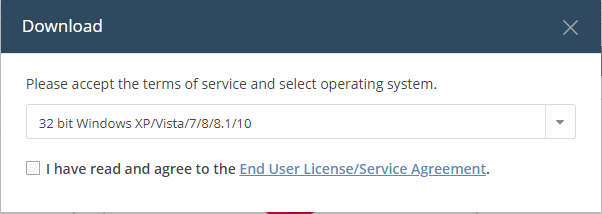
- Click 'Download' to get the tool
Next, transfer the setup file to your server and install. For more details on how to install and use the application, see https://help.comodo.com/topic-452-1-953-13328-Introduction-to-Network-Assessment-Tool.html.
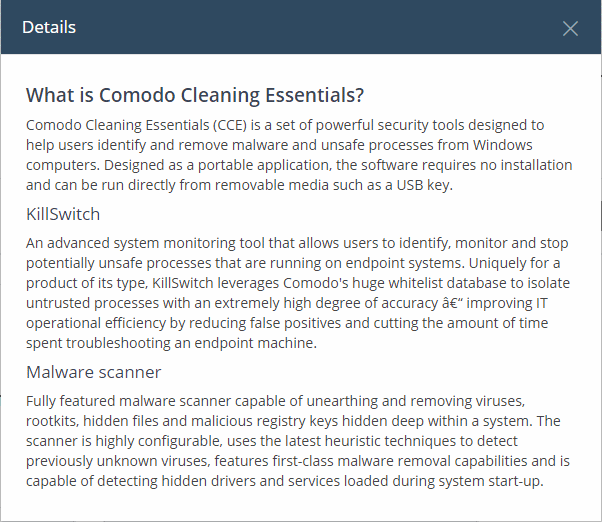
Xcitium Cleaning Essentials (XCE) is a set of computer security tools designed to help users identify and remove malware and unsafe processes from infected Windows computers. XCE is a portable application which requires no installation.
Major features include:
- Malware scanner - Fully customizable scanner capable of unearthing and removing viruses, rootkits, hidden files and malicious registry keys hidden deep in your system.
- KillSwitch - an advanced system monitoring tool that allows users to identify, monitor and stop any unsafe processes that are running on their system.
- Autorun Analyzer - An advanced utility
to view and handle services and programs that were loaded when your
system booted-up.
For more details on using the application, see https://help.comodo.com/topic-119-1-328-3516-Introduction-to-Comodo-Cleaning-Essentials.html.
Download XCE
- Click 'Tools' in the top-menu
- Click the 'Info' button in the 'Xcitium Cleaning Essentials' tile to view a description of the product:
- Click
the 'Download' button.
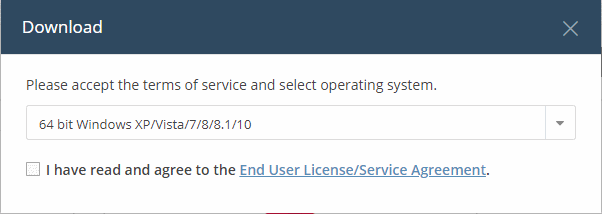
- Windows version - select the version appropriate to the endpoints on which you want to use XCE.
- Click the 'End User License/Service Agreement' link, read the EULA fully and select the check box to agree to it. The 'Download' button will appear after you agree to the EULA.
- Click
'Download' to get the tool.
For more help to use XCE, see https://help.comodo.com/topic-119-1-328-3516-Introduction-to-Comodo-Cleaning-Essentials.html.
- Unknown File Hunter (UFH) is a lightweight scanner which identifies unknown, potentially malicious, files on your network.
- After scanning your systems, it classifies all audited files as 'Safe', 'Malicious' or 'Unknown'.
- 'Safe' files are OK and 'Malicious' files should be quarantined or deleted.
- 'Unknown' files are those which cannot be classified as 'safe' or 'malicious'. All viruses and zero-day threats start life as an 'Unknown' file.
- UFH
lets you upload these files to our Valkyrie servers for analysis.
Valkyrie tests unknown files with a battery of run-time tests to
reveal whether or not they are harmful. You can view the results of
these tests in the UFH interface.
For
more details on
the application, see https://help.comodo.com/topic-400-1-794-10426-Introduction-to-Comodo-Unknown-File-Hunter.html
Auto Discovery and Deployment Tool
- Remotely deploy applications to multiple endpoints via Active Directory, Workgroup or IP address/IP range/host name.
- The utility can be used to remotely install .exe, .msi or .mst packages.
- ADDT is a portable app which does not require installation. Simply double-click on ADDT.exe to run the application.
Download the Auto Discovery and Deployment tool
- Click 'Tools' in the top-menu
- Locate the 'Auto-Discovery and Deployment' tile
- Click the 'Download' button
- Agree to the terms and conditions
- Click 'Download':
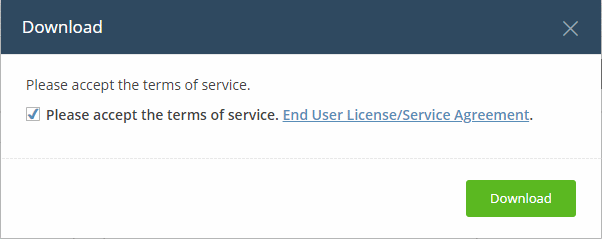
- Simply
open the file to run the application - no installation is required.
Remote Control by ITarian
- Remotely access Windows and Mac endpoints enrolled to Endpoint Manager.
- From here, you can solve issues, install third party software, run system maintenance and more.
Download the remote control tool
- Click 'Tools' in the top-menu
- Locate the 'Remote Control' tile
- Click the 'Download' button.
- Select the operating system of the admin computer on which you wish to install the tool.
- Click the 'Download' button:
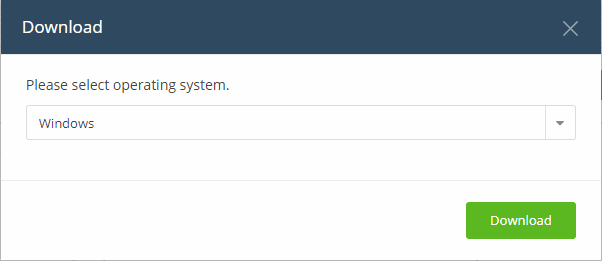
For more details about using the application, see https://help.comodo.com/topic-399-1-786-12348-Download-and-Install-the-Remote-Control-Tool.html
- Standalone tool to remotely gain access to the client computer
- Enables you to immediately troubleshoot issues, access files on network endpoints, run system maintenance and more.
Download the ITarian Remote Access tool
- Click 'Tools' in the top-menu from the computer you want to control
- Locate the 'ITarian Remote Access Tool' tile
- Click the 'Download' button.
- Select the file from your 'Downloads' folder and
- Agree to the terms and conditions
- Click 'Install':
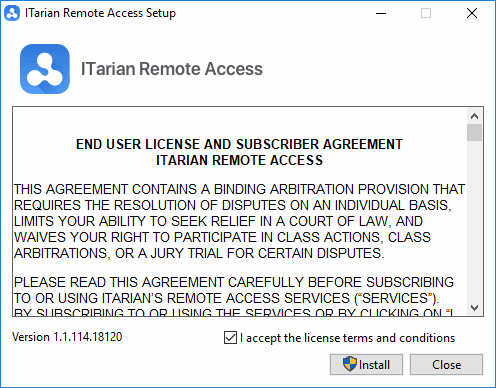
Agent Removal Tool
- The CCS removal tool is used to uninstall Comodo products that you are having difficulties removing with the normal Windows uninstaller. The tool is designed for Windows only.
- It scans the entire target system and removes Comodo application files, drivers, dlls and registry entries. It also creates a system restore point prior to performing the uninstall.
- This tool should only be used if you are having difficulties removing CCS or other Comodo products via Windows control panel.
- Click 'Tools' in the top-menu
- Locate the 'CCS Removal Tool' tile
- Click the 'Download' button.
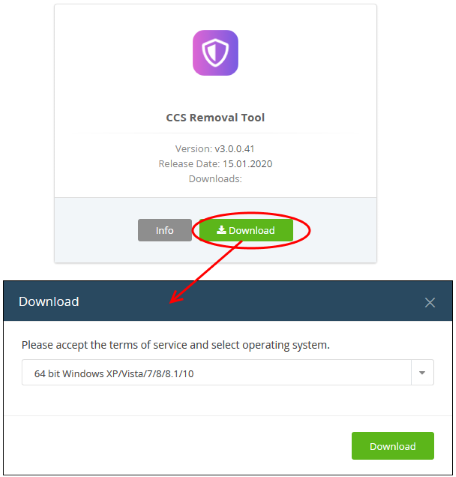
- Select the operating system of the device on which you wish to use the tool.
- Click 'Download' and save the tool.
- Transfer the tool to the device on which the CCS is to be removed.
- Run the CCS removal tool
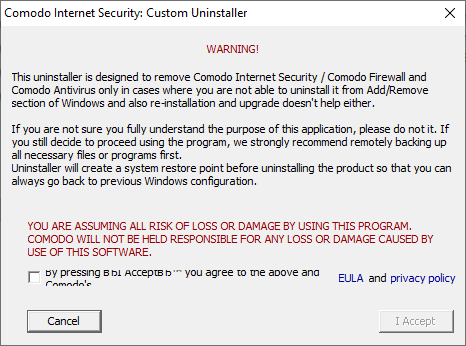
- Read the advisory, agree to the EULA then click 'I accept' to continue:
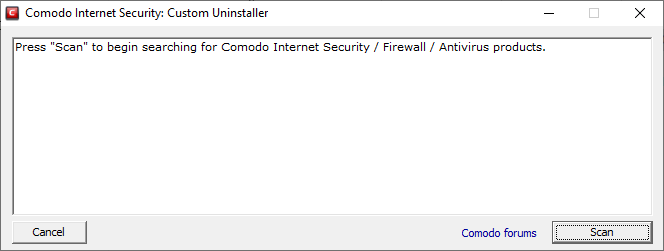
- Click 'Scan' to search for Comodo security products.
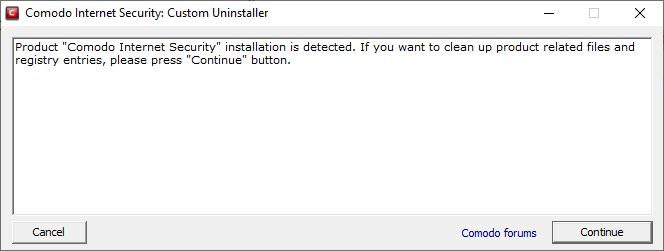
- Click 'Continue' to remove the items, if If the tool detects any of the specified products
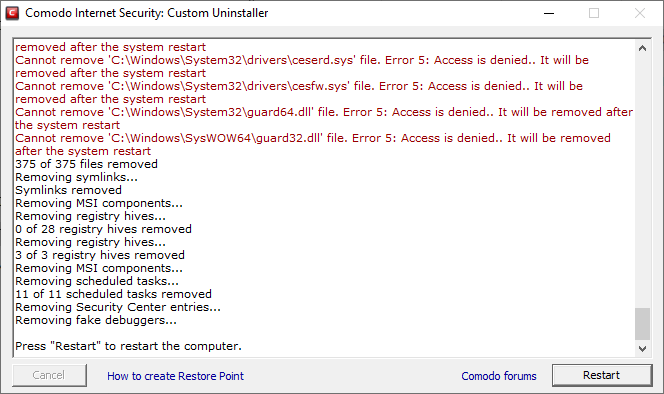
- Click 'Restart' after the uninstallation process is complete
- The tool requires a second restart to finalize the removal.
Uninstall CCS using Endpoint Manager
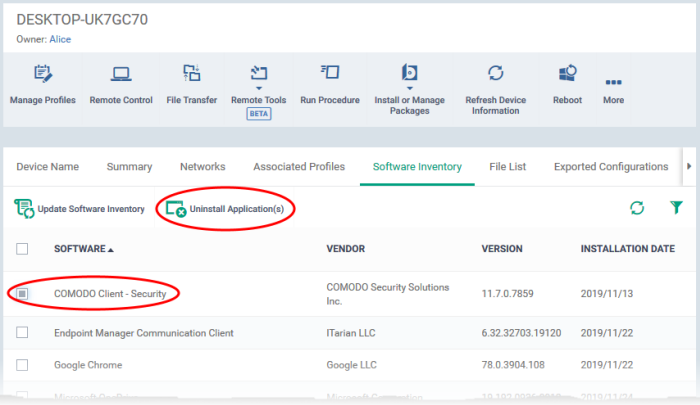
- Click 'Devices' > 'Device List' > 'Device Management'
- Select a company or group on the left to view devices in the group
Or
- Select 'Show All' to view every device enrolled to EM
- Click the name of a Windows device to open its device details interface
- Click the 'Software Inventory' tab
- Select 'Comodo Client – Security'
- Click 'Uninstall Application(s)' from the top.
Uninstall CCS locally using the control panel
- Type 'Add/Remove Programs' into the Windows search box
- Windows 10 – The search box is pinned to the task bar
- Windows 7 and other versions - Click the 'Start' button to view the search box
- Locate the Comodo product you wish to remove in the list of programs
- Click 'Uninstall'.


