Stealth your Computer Ports
- Click
'Tasks' > 'Firewall Tasks' > 'Stealth Ports'
- Port stealthing is a security feature which hides your ports to the outside world, providing no response to port scanners
|
What is a port? Your computer sends and receives data through an interface called a 'port'. There are over 65,000 numbered ports on every computer - with certain ports being traditionally reserved for certain services. For example, your machine almost definitely connects to the internet using ports 80 and 443. Your email application connects to your mail server through port 25. A 'port scanning' attack consists of sending a message to each of your computer ports, one at a time. This information is used by hackers to find out which ports are open, and which ports are being used by services on your machine. With this knowledge, a hacker can determine which attacks are likely to work against your machine. |
-
Stealthing a port effectively makes your computer invisible to a port scan. This differs from simply 'closing' a port as NO response is given to any connection attempt. A closed port responds with a 'closed' reply, which reveals that there is a PC in existence.
- If a hacker or automated scanner cannot 'see' your computer then they will move on to other targets. You can still connect to the internet and transfer information as usual, but remain invisible to outside threats.
Stealth
ports on your computer:
- Click 'Tasks'> 'Firewall Tasks'
- Click 'Stealth Ports'
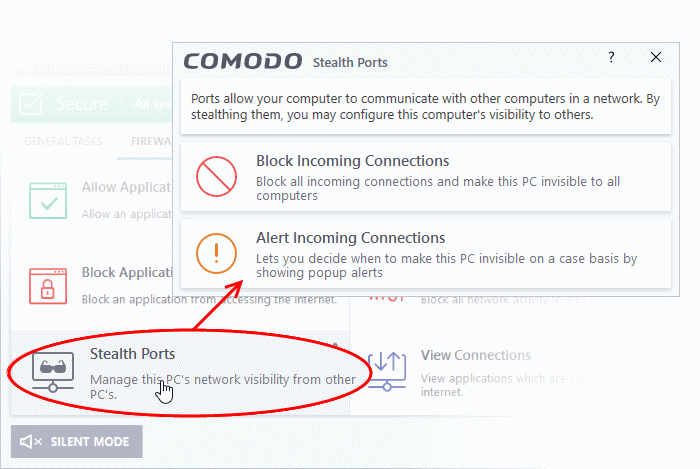
- Block incoming connections - Your computer's ports are invisible to all networks, regardless of whether you trust them or not. The average home user (using a single computer that is not part of a home LAN) will find this option the most convenient and secure. You are not alerted when the incoming connection is blocked, but the rule adds an entry to the firewall event log file. Specifically, this option adds the following rule in the 'Global Rules' interface:
Block And Log| IP | In| From Any IP Address| To Any IP Address | Where Protocol is Any
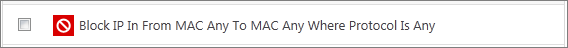
If you would like more information on the meaning and construction of rules, please click here.
- Alert incoming connections - You will see a firewall alert every time there is a request for an incoming connection. The alert asks your permission on whether or not you want the connection to proceed. This can be useful for peer-to-peer and remote desktop applications which need to access your points in order to connect. Specifically, this option adds the following rules in the 'Global Rules' interface:
Block ICMPv4 In From [Any IP Address] To [Any IP Address] Where Message is [Message]
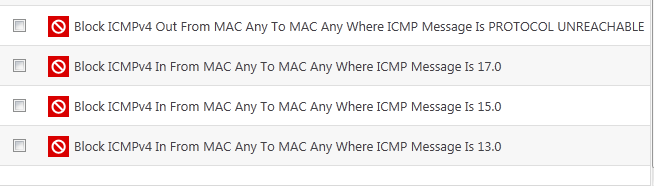
If you would like more information on the meaning and construction of rules, please click
here.


