Miscellaneous Settings
- Click 'Settings' > 'Advanced Protection' > 'Miscellaneous'
- The miscellaneous settings panel lets you:
- Configure protection against shellcode injections (buffer overflow attacks)
- Skip automatic cleanup of suspicious certificates.
- Configure protection settings for auto-start entries and scheduled tasks
Open 'Miscellaneous' settings:
- Click 'Settings' on the CCS home screen
- Click
'Advanced Protection'
> 'Miscellaneous'
This interface allows you to:
Disable shellcode injection detection
By default, protection against shellcode injection is enabled for all applications on your computer. Use this setting to define applications which you do not want to monitor for shellcode injections.
|
Background:
|
Exclude certain applications from shellcode injection protection
- Make sure 'Don't detect shellcode injections in these applications' is enabled then click the 'these applications' link. The 'Manage Exclusions' dialog appears
- Click the 'Add' button at the top
You can add items by selecting the required option from the drop-down:
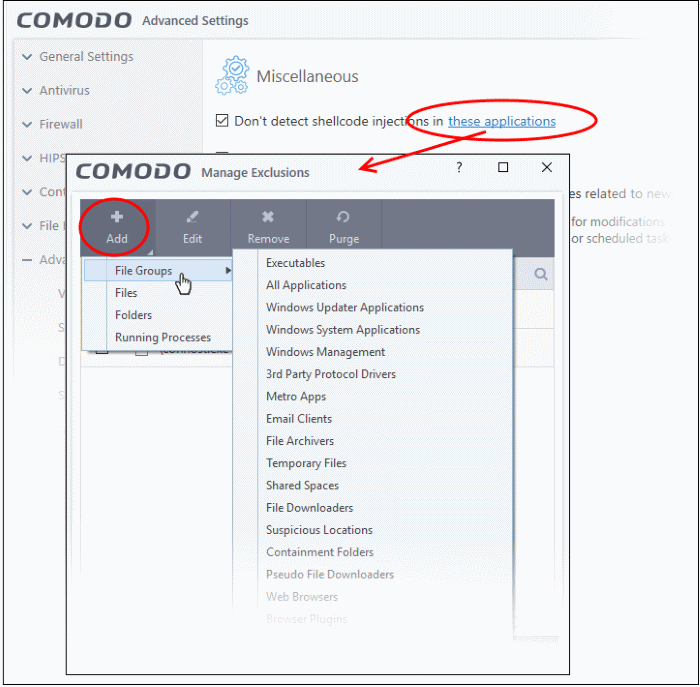
- File Groups - Select a category of pre-set files or folders. For example, 'Executables' lets you create a ruleset for all files with the extensions .exe .dll .sys .ocx .bat .pif .scr .cpl, *cmd.exe *.bat, *.cmd. Other categories available include 'Windows System Applications', 'Windows Updater Applications', 'Start Up Folders' etc. See File Groups for more details on file groups.
- Running Processes - Select an application or executable from the processes that are currently running on your PC.
- Folders - Specify a folder on your computer to include all files in the folder to the exclusions .
- Files - Select a specific executable file you wish to add to the exclusions.
Click 'OK' to implement your settings.
Do not automatically cleanup suspicious certificates
- Choose whether or not to delete any root certificates that were not signed by a trusted certificate authority
- By default, CCS warns you if any fake root certificates are found in your browsers but does not delete them
- Disable this option if you want CCS to delete those fake certificates whenever they are found
|
Background:
|
Define actions to be taken on unrecognized auto-start entries/scheduled tasks
- Apply the selected action to unrecognized autorun entries related to new / modified registry items - Specify what CCS should do if applications added to Scrip Analysis > Autoruns Scans try to create or modify one of the following registry items:
- Windows services
- Auto-start entries
- Scheduled tasks
The available options are:
- Ignore - CCS does not take any action (Default)
- Terminate - CCS stops the process / service
- Terminate and Disable - Auto-run processes are stopped and the corresponding auto-run entry removed. In the case of a service, CCS disables the service
- Quarantine and Disable - The application is quarantined and the corresponding auto-start entry is removed. In the case of a service, CCS disables the service.
|
Background:
|
Monitor processes and DLLs loaded atstart up:
- You can instruct CCS to identify untrusted DLLs, apps, portable executables (PE) and autoruns launched before CCS starts on the endpoint. These may expose the endpoint to a danger if those items turn to be malicious.
- By default, CCS does not monitor these items.
- CCS checks whether startup items are signed by a trusted authority and marks them as trusted or untrusted. The flag is used at next restart to allow or block the item.
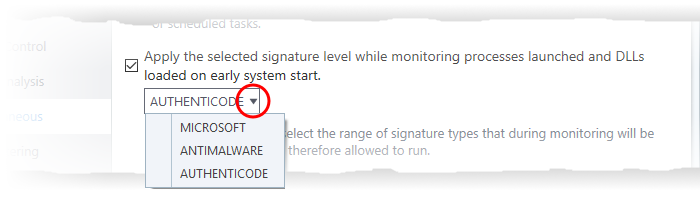
- Microsoft - Only items signed by Microsoft certificates are marked as trusted
- Antimalware - Trusts files signed by either Microsoft or Antimalware certificates
- Authenticode - Flags all signed files as trusted
Monitor DLL files loaded by currently running processes
- By default, CCS does not monitor the DLL files loaded to system memory, by processes that are currently running on the endpoint.
Monitor DLL files being loaded by running processes–If enabled, CCS runs a file rating scan on each DLL loaded to identify its trust rating
- The trust rating is reported to Endpoint Manager and added to local logs. Files with an Unrecognized' rating are submitted to Valkyrie for analysis
- You can view these details at 'Security Sub-Systems' > 'Application Control'
- See https://help.comodo.com/topic-399-1-786-10102-Manage-File-Trust-Ratings-on-Windows-Devices.html for more details
- Self-Protection Options: Allows to protection for Xcitium Client - Security agent's own processes and assets. (Default = Enabled).
- Protect comodo files - Access to blocking protected folders (CCS folders), driver/guard dll files.
- Protect comodo Registry key – Allows you to protect system critical registry keys against modification.
- Protect comodo processes - Access blocking to processes (XCS processes) with write/terminate permissions and on win10and block loading unsigned DLLs into processes (XCS processes).
- Audit Only - The audit mode sends a notification about access to protected folders (xcs folders), drivers/guard dll files, notification about access to services in the registry, (XCS processes) with write/terminate permissions and loading unsigned DLLs into processes (CCS processes).
- Click 'OK' to save your settings.


