Run a Rating Scan
- Click 'Tasks' > 'General Tasks' > 'Scan' > 'Rating Scan'
- A rating scan checks the trust-rating of files on your computer.
- Trust ratings are as follows:
- Trusted - The file is safe to run.
- Malicious - The file is malware. Depending on your settings, CCS will either quarantine the file immediately or present you with disinfection options.
- Unrecognized – Comodo does not currently have a trust rating for the file. Unrecognized files should be run in the container to prevent them potentially attacking your computer. You can simultaneously submit them to Comodo for a trust-rating analysis.
Run a Rating scan
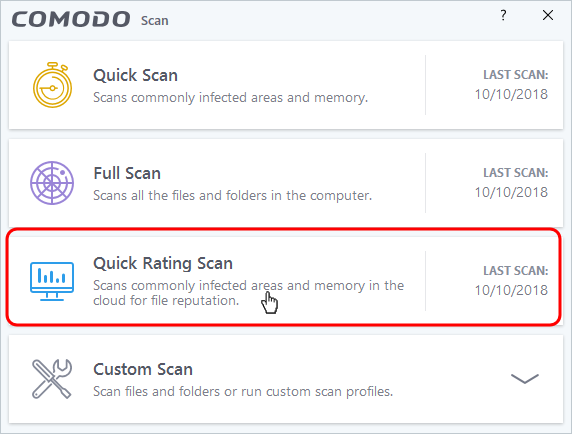
- Click the 'Scan' tile on the CCS home screen (click here for alternative ways to open the scan interface)
- Select 'Ratings Scan':
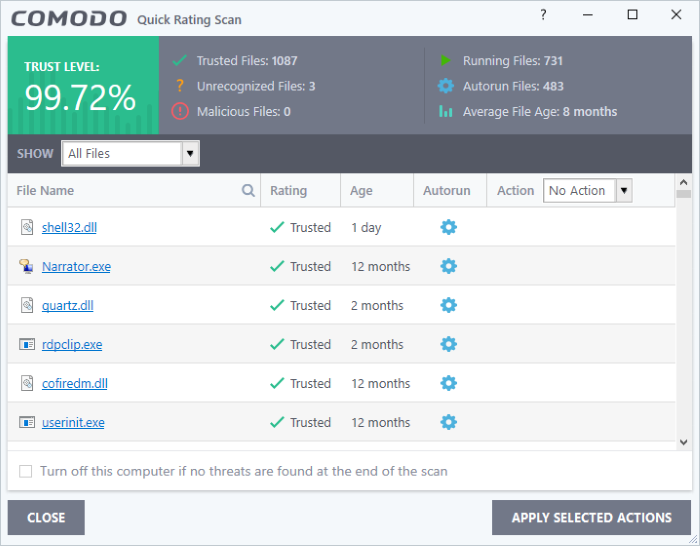
CCS will analyze all files on your computer and assign them a trust rating. File ratings are shown in the results table at the end of the scan:
|
Rating Scan Results Table - Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
File Name |
The label of the scanned item. |
|
Rating |
The trust level of the file as per the cloud based analysis. The possible values are:
|
|
Age |
The length of time the item has been on your computer. |
|
Auto-run |
Whether or not the file automatically runs without user intervention. |
|
Action |
Select how you want to deal with the listed item. See the explanations given below: |
The drop-down menus on the right let you handle unrecognized and malicious items:
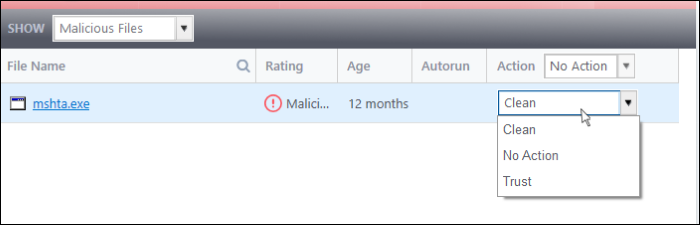
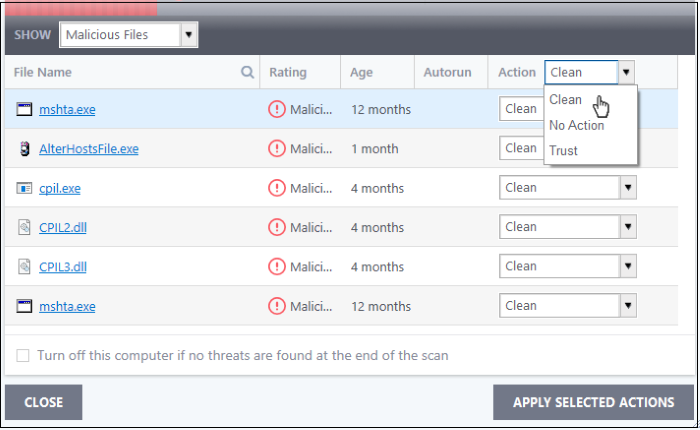
- Clean - Available only for malicious items. The threat is placed in quarantine for your review. Click 'Tasks' > 'General Tasks' > 'View Quarantine' to open this area. You can restore or permanently delete files from quarantine as required. See Manage Quarantined Items for more details.
- No Action – Ignores the warning this time only. The file not placed in quarantine. Use this option with caution. The file will be caught again by the next rating scan you run.
- Trust – The file is awarded trusted status in the File List ('Settings' > 'File Rating' > 'File List'). The file will be excluded from any future rating scans. Only select this option if you are sure the item is trustworthy.
- CCS logs all actions taken in the results screen. You can view the logs at 'Tasks' > 'Advanced Tasks' > 'View Logs'. See File List Changes Logs for more details.
- Use the drop-down in the 'Action' column header to apply your choice to all listed files: