- Introduction To Comodo Client Security
- General Tasks - Introduction
- Firewall Tasks - Introduction
- Containment Tasks - Introduction
- DLP Tasks - Introduction
- Advanced Tasks - Introduction
- Create A Rescue Disk
- Remove Deeply Hidden Malware
- Manage CCS Tasks
- View CCS Logs
- Antivirus Logs
- VirusScope Logs
- Firewall Logs
- HIPS Logs
- Containment Logs
- Website Filtering Logs
- Device Control Logs
- Autorun Event Logs
- Alert Logs
- CCS Tasks Logs
- File List Changes Logs
- Vendor List Changes Logs
- Configuration Change Logs
- Virtual Desktop Event Logs
- Data Loss Prevention Event Logs
- Search And Filter Logs
- Submit Files For Analysis To Comodo
- View Active Process List
- CCS Advanced Settings
- Appendix 1 - CCS How To... Tutorials
- Enable / Disable AV, Firewall, Auto-Containment And VirusScope Easily
- Set Up The Firewall For Maximum Security And Usability
- Block Internet Access While Allowing Local Area Network (LAN) Access
- Block / Allow Specific Websites To Specific Users
- Set Up HIPS For Maximum Security And Usability
- Create Rules To Auto-Contain Applications
- Run An Instant Antivirus Scan On Selected Items
- Create An Antivirus Scan Schedule
- Run Untrusted Programs Inside The Container
- Run Browsers Inside The Container
- Restore Incorrectly Quarantined Item(s)
- Submit Quarantined Items To Comodo Valkyrie For Analysis
- Enable File Sharing Applications Like BitTorrent And Emule
- Block Any Downloads Of A Specific File Type
- Disable Auto-Containment On A Per-application Basis
- Switch Off Automatic Antivirus Updates
- Suppress CCS Alerts Temporarily
- Control External Device Accessibility
- Appendix 2 - Comodo Secure DNS Server
- About ITarian
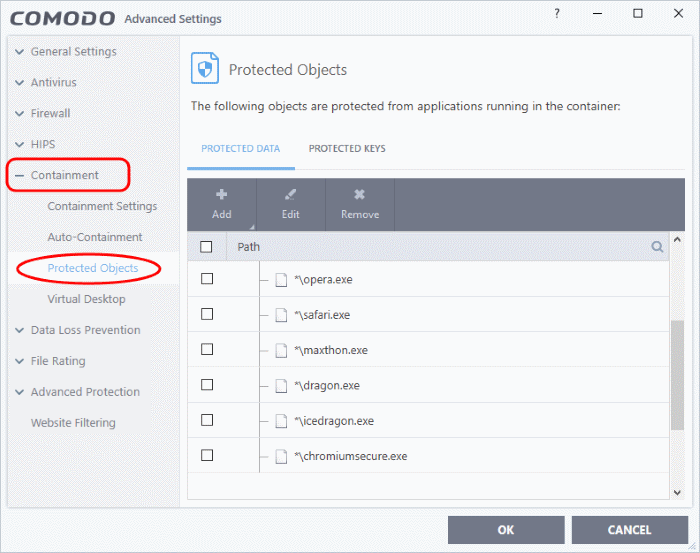
Protected Objects - Containment
- Click 'Settings' > 'Containment' >'Protected Objects'
- Items that you add to this area cannot be read or modified by applications running in the container.
- Examples items you can add are files, folders and registry keys.
- This
prevents unknown/untrusted applications from causing damage to, or
stealing data from, important items.
Click the following links for more details:


