Script Analysis Settings
- Click 'Settings' > 'Advanced Protection' > 'Script Analysis'
- The script analysis settings panel lets you:
- Configure heuristic command line analysis for applications in real-time
- Configure heuristic command line analysis for auto-run entries. Auto-run entries include Windows services, auto-start items and scheduled tasks.
|
Background note: 'Heuristics' is a technology which analyzes a file to see if it contains code typical of a virus. Heuristics is about detecting 'virus-like' traits in a file. This helps to identify previously unknown (new) viruses. |
Open the
'Script Analysis' settings panel
- Click 'Settings' on the CCS home screen
- Click 'Advanced Protection' > 'Script Analysis'
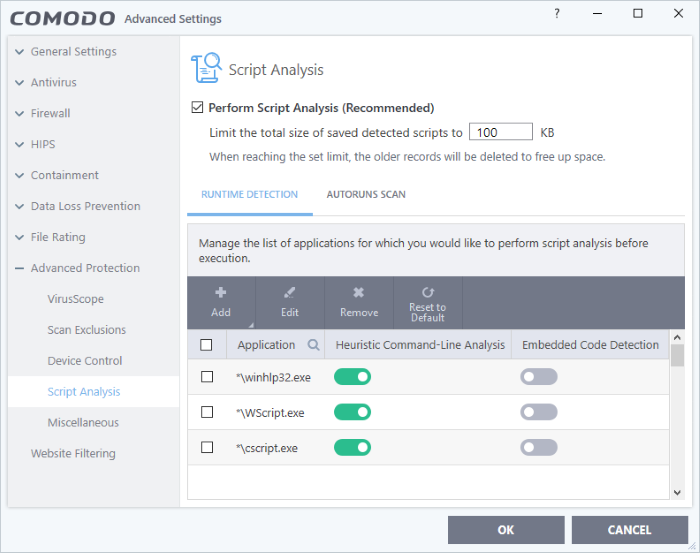
- Perform Script Analysis (Recommended) - Enable / disable script analysis of managed applications (Default = Enabled)
- Limit the total size of saved detected scripts to 'N' KB - CCS stores the list of executing scripts that are run by the managed applications for analysis. This options allows you to specify the total size of the stored scripts. When the set limit is reached, the older scripts are deleted automatically.
The interface has two tabs:
CCS performs heuristic analysis on certain programs because they are capable of executing code. Example programs are wscript.exe, cmd.exe, java.exe and javaw.exe. Example code includes Visual Basic scripts and Java applications.
- For example, the program wscript.exe can be made to execute Visual Basic scripts (.vbs file extension) via a command similar to 'wscript.exe c:/tests/test.vbs'.
- If this option is selected, CCS detects c:/tests/test.vbs from the command-line and applies all security checks based on this file. If test.vbs attempts to connect to the internet, for example, the alert will state 'test.vbs' is attempting to connect to the internet
- If this option is disabled, the alert would only state 'wscript.exe' is trying to connect to the Internet'.
- Relevant
settings are applied to the scripts. For example, if a script is
detected by the containment module, then auto-containment rules are
applied. Each module (AV, FW,
VirusScope and so on) that detects a script will apply its
appropriate settings.

|
Runtime Detection - Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Application |
Names of existing applications covered by this rule. |
|
Heuristic Command-Line Analysis |
Enable or disable command line tracking. |
|
Embedded Code Detection |
Enable or disable embedded code tracking. |
| Exclusions | Create exclude processes from blocked by embedded code/ command line using the regular expressions |
Manually add a new application to the list for analysis
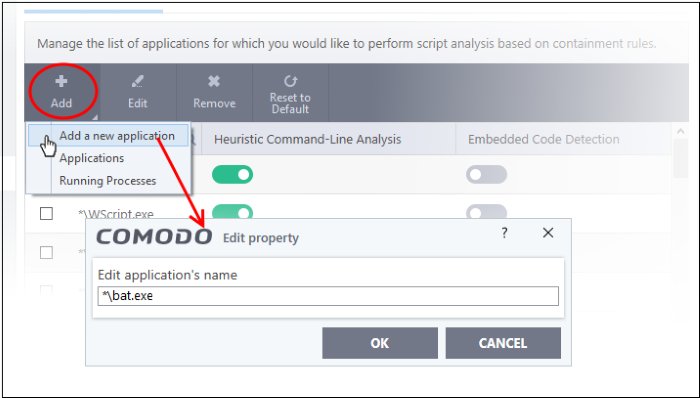
- Click
'Add' at the top
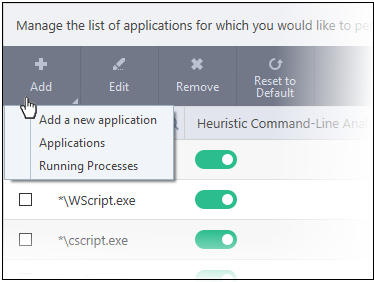

You can add an application by following methods:
- Click 'Add new application' from the 'Add' drop-down
- Enter the file path in the 'Edit Property' dialog and click 'OK'

The application will be added and displayed in the list.
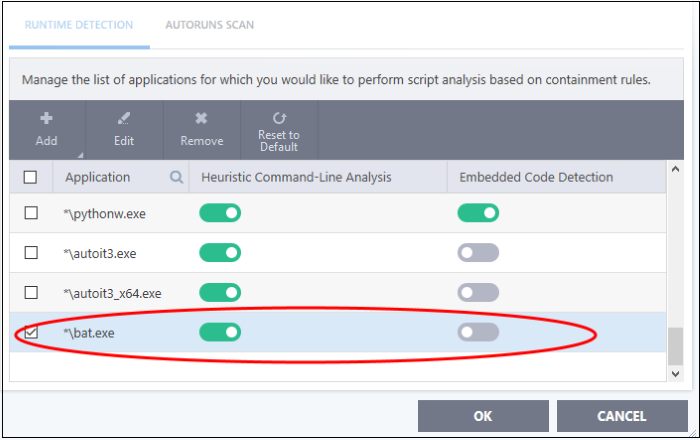

- Click
"OK" to apply your settings
- Click 'Add' then 'Applications' from the drop-down
- Navigate to the file you want to add in the 'Open' dialog and click 'Open'
- The file will be added to the list
- Click
"OK" to apply your settings
Add a currently running processes
- Choose 'Running Process' from the 'Add' drop-down
- A list of currently running processes in your computer will be displayed
- Select the process whose parent application you wish to add for analysis
- Click 'OK' from the 'Browse for Process' dialog
- The application will be added to the list
- Use the slider beside the applications to enable/disable them for analysis.
- Click the 'Edit' button to update the details of an application.
- To remove an application, select it from the list and choose 'Remove' at the top.
- To reset to default applications for analysis, click 'Reset to Default' at the top.
- Click
'OK' at the bottom to apply your changes.
Add Exclusions
- You can be able to exclude and log the
command line detected by script analysis by defining a regular expression on
CCS. The detected but excluded items shall be able to log
as "ignored"
- Click ‘Add’ at the top
- Enter an expression which you want to exclude for ex : "C:Users"
- Specify the type of regular expression of data need to add.
- Single Character– Regular expressions are patterns that match a single character. Most
characters, including all letters ( a-z and A-Z ) and digits ( 0-9 ), match
itself. For example, the regex s matches substring "s" , z matches
"z" , and 9 matches "9"
- Multiple Characters- Regex that match the multiple characters like # and %, /=
- Fixed length – Fixed regular regex that you cannot exceed to match regix after the defined length
- Symbol Types – We are using different types of letters, digits and customs symbols in regular expressions
For ex :
1) [...]: Accept ANY ONE of the character within the square bracket, e.g., [aeiou] matches "a", "e", "i", "o" or "u"
2) All characters, except those having special meaning in regex, matches themselves. E.g., the regex x matches substring "x"; regex 9 matches "9"; regex = matches "="; and regex @ matches "@".
- Click ‘Custom symbols’ to make your own regex. Enter any symbols you need to add
- Data Patterns – You can select any
of the patterns from the list. The path shows any of the file or folder path
like “C:UsersPublicDocuments” or add an email address or URL data patterns
- Click ‘Generate Regular Expression’ to add a new one.
- Click ‘Ok’ to save your changes
Edit an Exclusions
- Select an expression to edit > Click ‘Edit’
- Edit the regex where you need to change
- Click ‘Ok’ to save your changes
Delete an Exclusions
- Select an expression to edit > Click ‘Remove’
- The selected regex will be removed
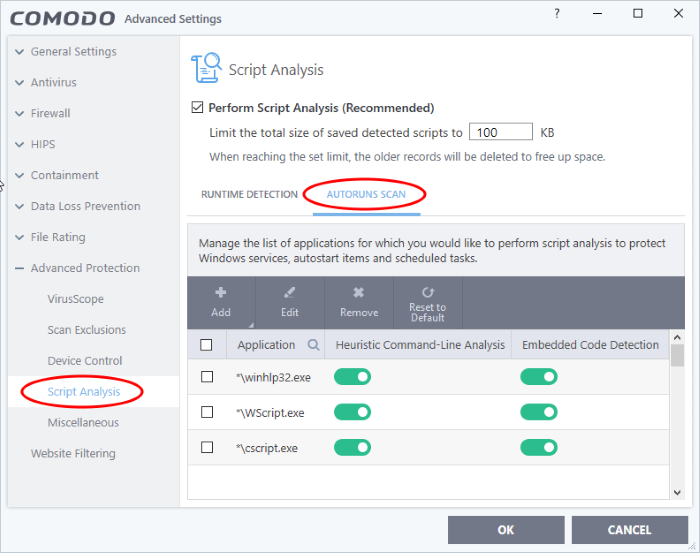
- Add and manage applications for which you want to perform heuristic command-line analysis and embedded code detection in order to protect Windows services, autostart items and scheduled tasks.
- CCS ships with a list of predefined applications for which it performs heuristic analysis on programs that are capable of executing code.
- The applications added here are applicable for the settings in:
- 'Scan Options' > 'Apply this action to suspicious autorun processes' (monitors only during on-demand scans)
- 'Advanced Settings' > ' Miscellaneous' > 'Apply the selected action to unrecognized autorun entries related to new/modified registry items ' (monitors constantly)
Open the 'Autoruns Scans'
interface
- Click
'Settings' on the CCS home tasks screen
- Click
'Advanced Protection'
> 'Script Analysis'
|
Autroruns Scans - Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Application |
Names of existing applications covered by this rule. |
|
Heuristic Command-Line Analysis |
Enable or disable command line tracking. |
|
Embedded Code Detection |
Enable or disable embedded code tracking. |
| Exclusions | Create exclude processes from blocked by embedded code/ command line using the regular expressions |
Manually add a new application to the list for analysis
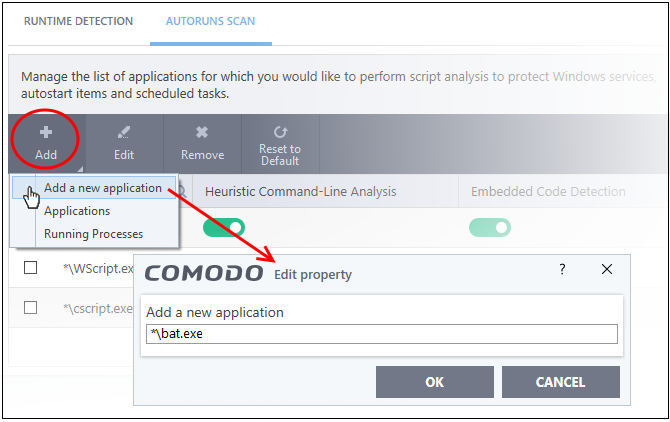
- Click 'Add' at the top
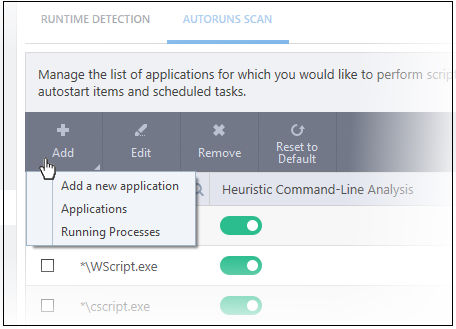

You can add an application by following methods:
- Click 'Add new application' from the 'Add' drop-down
- Enter
the file path in the 'Edit Property' dialog and click 'OK'

The
application will be added and displayed in the list.
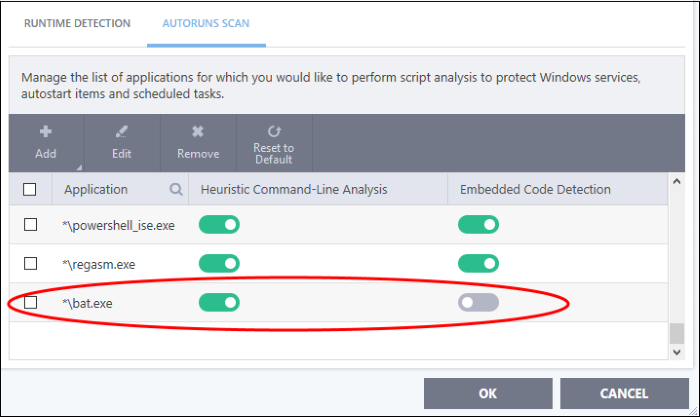

- Click
"OK" to apply your settings
- Click 'Add' then 'Applications' from the drop-down
- Navigate to the executable file you want to add in the 'Open' dialog and click 'Open'
- The file will be added to the list
- Click
"OK" to apply your settings
Add a currently running processes
- Choose 'Running Process' from the 'Add' drop-down
- A list of currently running processes in your computer will be displayed
- Select the process whose parent application you wish to add for analysis
- Click 'OK' from the 'Browse for Process' dialog
- The application will be added to the list
- Use the slider beside the applications to enable/disable them for analysis
- Click the 'Edit' button to update the details of an application
- To remove an application, select it from the list and choose 'Remove' at the top
- To reset to default applications for analysis, click 'Reset to Default' at the top
- Click
'OK' at the bottom to apply your changes.
Add Exclusions
- You can be able to exclude and log the command line detected by script analysis by defining a regular expression on CCS. The detected but excluded items shall be able to log as "ignored"
- Click ‘Add’ at the top
- Enter an expression which you want to exclude for ex : "C:Users"
- Specify the type of regular expression of data need to add.
- Single Character– Regular expressions are patterns that match a single character. Most characters, including all letters ( a-z and A-Z ) and digits ( 0-9 ), match itself. For example, the regex s matches substring "s" , z matches "z" , and 9 matches "9"
- Multiple Characters- Regex that match the multiple characters like # and %, /=
- Fixed length –
- Symbol Types – We are using different types of letters, digits and customs symbols in regular expressions
For ex :
1) [...]: Accept ANY ONE of the character within the square bracket, e.g., [aeiou] matches "a", "e", "i", "o" or "u"
- Click ‘Custom symbols’ to make your own regex. Enter any symbols you need to add
- Data Patterns – You can select any of the patterns from the list. The path shows any of the file or folder path like “C:UsersPublicDocuments” or add an email address or URL data patterns
- Click ‘Generate Regular Expression’ to add a new one.
- Click ‘Ok’ to save your changes
Edit an Exclusions
- Select an expression to edit > Click ‘Edit’
- Edit the regex where you need to change
- Click ‘Ok’ to save your changes
Delete an Exclusions
- Select an expression to edit > Click ‘Remove’
- The selected regex will be removed


