Start Comodo Client Security
After installation, Comodo Client Security automatically starts whenever you start Windows.
CCS has two modes:
- Normal Mode - Allows you to access the entire CCS interface.
- Virtual Desktop Only Mode - You can only open the Virtual Desktop and Virtual Desktop settings.
The
mode available to you depends on the Endpoint Manager (EM) profile
active on the device.
There are 5 different ways to open CCS if it is in normal mode:
- Click Start and select All Apps > Comodo > Comodo Client Security
(Please note the start menu varies slightly for different Windows versions.)
- Double-click the desktop shortcut to start Comodo Client Security. The shortcut is only visible if 'Show Desktop Shortcut' is enabled in the Endpoint Manager profile active on the endpoint.

- Click the information bar in the widget to start CCS. The shortcut is only visible if 'Show Widget' is enabled in the Endpoint Manager profile active on the endpoint.

The widget also contains other useful data and features. See 'The Widget' for more details.
- Double-click the shield icon to start the main interface.

You can also right-click on the tray icon and select 'Open...'.
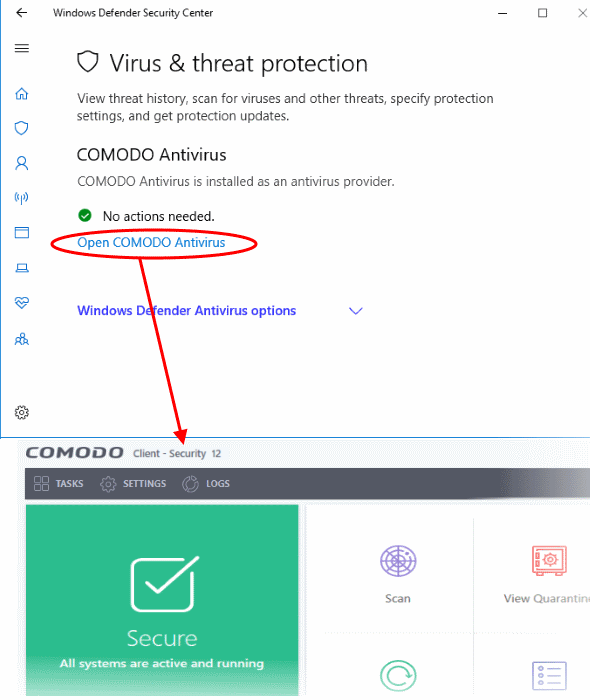
- Double-click on the Windows Defender icon to open the application
OR
- Right-click on the tray icon and select 'Open...'.

- Click the 'Virus & threat protection' tile
- Click
the 'Open COMODO Antivirus' to open the Comodo Client Security interface:
- This mode means you can only open the Virtual Desktop and access Virtual Desktop settings. You cannot access any other areas of the CCS interface.
- Endpoint Manager admins - You can enable or disable this setting in the ‘UI Settings’ section of a profile.
See https://help.itarian.com/topic-459-1-1005-14932-Communication-Client-and-Comodo-Client---Security-Application-UI-Settings.html if you want to read more on this.
In 'Virtual Desktop Only' mode:
- The system tray icon and the desktop widget are hidden
- The CCS desktop shortcut and Windows start menu entry lead to the following menu:
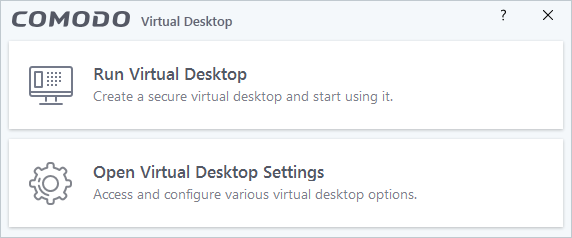
- Run Virtual Desktop - Opens the virtual desktop. See The Virtual Desktop for more help on this.
- Open Virtual Desktop Settings - Opens the virtual desktop settings area in CCS. See Virtual Desktop Settings for help with these settings.
End-users
cannot access any other area of CCS.
|
What is an Endpoint Manager Profile?
|


