Security Dashboards
- Click
'Security Sub-Systems' > 'Security Dashboards'
The security dashboard is a
list of all security events on managed endpoints. This includes
events from the antivirus, containment, application-control, autorun
control, and virtual desktop components.
- To view threats recorded on Android devices, go to ‘Security Sub-Systems’ > ‘Antivirus’ > ‘Android Threat History’
Endpoint Manager retains security event logs for 12 months for PCI-DSS compliance.
Events that are captured include:
Antivirus – Windows, Mac OS, and Linux devices
- File blocked, moved to quarantine, or ignored
- File restored/removed from quarantine
- File skipped by a virus scan
- File rated as trusted, or submitted as a false positive, at the scan results screen
- File
added to the exclusions list
Containment – Windows devices
- File blocked, ignored, or run in the container by:
- Auto-containment rules in the profile on the device
- A local user running the file in the container on a one-off basis
Application Control – Windows devices
- Unrecognized or malicious file added to, or removed from, the CCS 'File list'
- Changes to the trust rating of a file
- See Manage File Trust Ratings on Windows Devices for more details.
Autorun Control – Windows devices
- Records the action taken by CCS on apps that try to modify Windows services, startup entries, and scheduled tasks.
Recorded actions include:
- Ignore
- Terminate
- Terminated and disabled
- Quarantined and disabled
- Restored
- Deleted
Virtual Desktop - Windows devices
- Virtual desktop activity on endpoints
- Launched
- Terminated
- Session started
- Session paused
- Session continued
- Session terminated
- Switched to host
- Switched to virtual desktop
The interface also lets you rate files, view file details, and move files in or out of quarantine.
Open the dashboard:
- Click
'Security Sub-Systems' > 'Security Dashboards'
- Select a company or group to view devices in that group
Or
- Select 'Show all' to view every device enrolled to Endpoint Manager
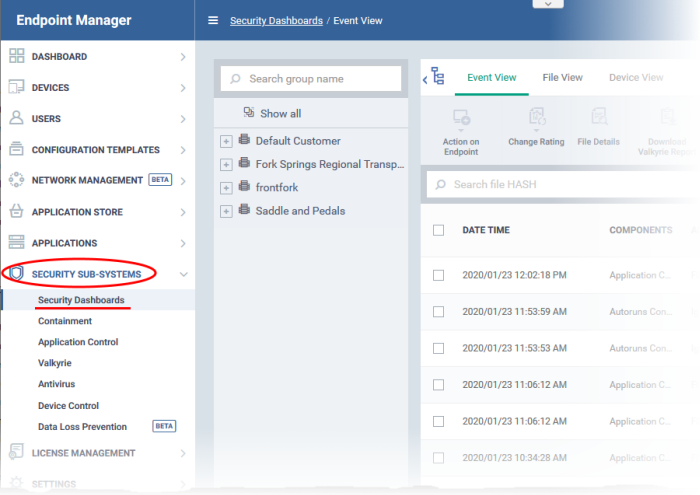
The dashboard has three tabs:
- Event View - Shows events in chronological order. See View Security Events by Time for more details.
- File View - View security events on specific devices. See View Security Events by File for more details.
-
Device View – Shows all events that occurred on specific devices. See View Security Events by Device for more information.


