View and Manage Quarantined Items
- Quarantine is a secure holding area for potentially dangerous files. Quarantined files pose no threat to your system.
- You can delete or restore quarantined items, or assign a file rating to them.
- File ratings determine how CCS handles the file:
- Files rated as 'Malicious' will stay in quarantine on the device.
- Files rated as 'Unrecognized' will be restored to their original locations on the device. Future virus scans may flag them as malicious again.
- Files rated as 'Trusted' will be restored to their original locations on the device. These files are skipped in future virus scans.
|
How do threats quarantined? Windows Devices Real time scans - Threats are placed in quarantine if:
On-demand / Scheduled scans - Threats are placed in quarantine if:
DLP Scans
Manual quarantine:
MAC OS Devices Real time scans - Threats are placed in quarantine if:
On-demand / Scheduled scans - Threats are quarantine if:
Manual quarantine:
Linux Devices Real time scans - Threats are quarantine if:
On-demand / Scheduled scans - Threats will be placed in quarantine if:
Manual quarantine:
Items moved to quarantine are encrypted and not allowed to run. |
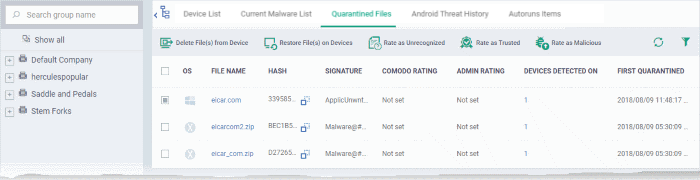
Open the quarantine interface
- Click 'Security Sub-Systems' > 'Antivirus'
- Click the 'Quarantined Files' tab
- Select a company or a group to view malware identified on their devices
Or
- Select 'Show All' on the left menu to view malware identified on all devices enrolled to EM
|
'Quarantine Files' - Table of Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
OS |
The operating system of the device at which the item was quarantined. |
|
File Name |
The file that was moved to quarantine.
|
|
Hash |
The SHA1 hash value of the quarantined file
|
|
Signature |
The name of the identified malware. 'User Item' indicates the file was moved to quarantine manually by the user on the endpoint. |
|
Comodo Rating |
The file's trust level as rated by CCS. |
|
Admin Rating |
The trust rating of the file as set by the administrator. Files can be rated as trusted, malicious or unrecognized. |
|
Devices Detected On |
The number of devices on which the item was quarantined.
|
|
First Quarantined |
Date and time at which the malware was identified and quarantined the first time. |
The quarantine interface allows you to:
View Details of a Quarantined Item
- Click 'Security Sub-Systems' > 'Antivirus' > 'Quarantined Files'
- Click on the file name of an item in the list:
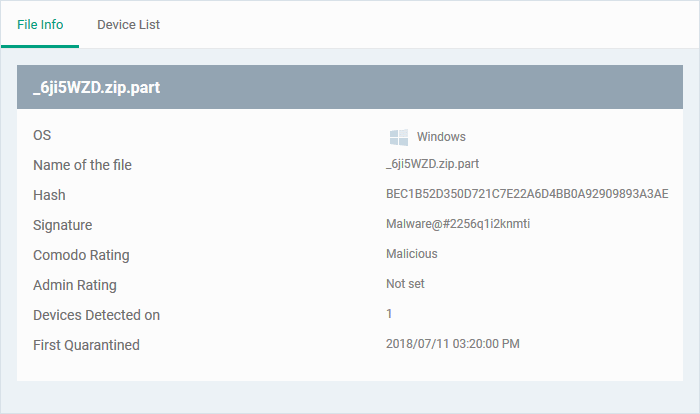
- This will open the file details interface which shows:
- File Info - General information such as OS, file-name, hash, file rating, number of devices on which the file was quarantined, and more.
- Device List - Shows list of endpoints upon which the file was found with their details like installation path of the file on each device, the device owner and the date and time at which the file was quarantined.
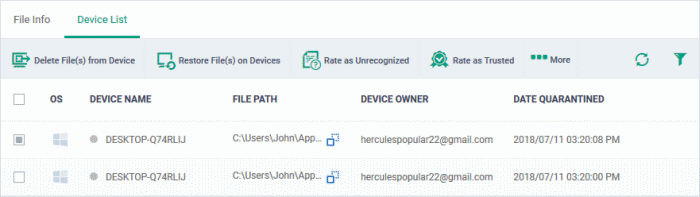
The options on the top let you to:
- Restore False Positives from Quarantine on a device
- Remove the item from a device
- Rate files as 'Unrecognized', 'Trusted' or 'Malicious'
- See the following sections for more details
- If your review confirms that a quarantined item is a genuine threat then it can be deleted from endpoints.
- Conversely, if an item is is found to be a false positive, you can restore it to its original location.
- You can also rate a file as unrecognized, trusted or malicious based on your assessment. The new verdict will be sent to all endpoints and will be reflected in the 'Unrecognized' and 'Trusted' interfaces.
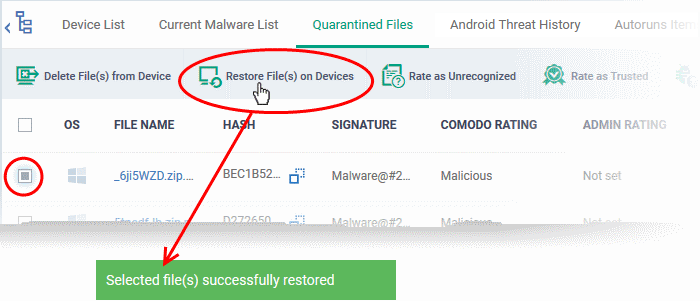
Restore False Positives from Quarantine
- If the identified item is a false positive, select the item from the list and click 'Restore File(s) on Devices' from the options at the top.
The item will be restored to its original location on all devices and removed from the list.
Remove Malware files from the devices
- Select the item(s) from the list and click 'Delete File(s) From Device' from the options at the top.
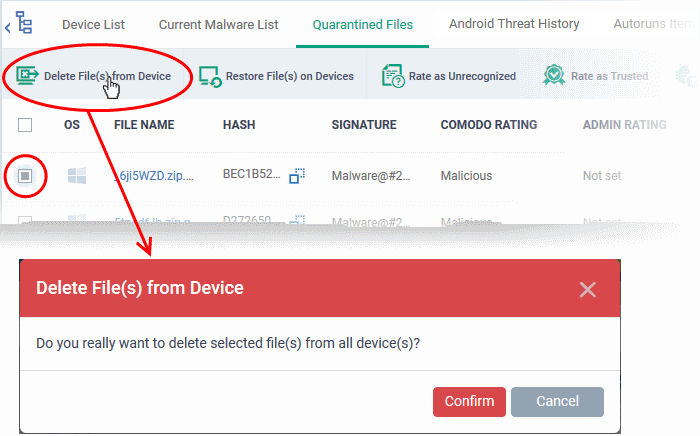
- Click 'Confirm' in the confirmation dialog.
The file will be deleted from all devices at which it was quarantined and removed from the list.
Rate
files as 'Unrecognized', 'Trusted' or 'Malicious'
- If the rating of a quarantined file is changed to 'Trusted' or 'Unrecognized', the file is restored to its original location. The new rating is also stored in the CCS database on the devices.
- To change the rating of a quarantined file, select it and click the appropriate button at the top:
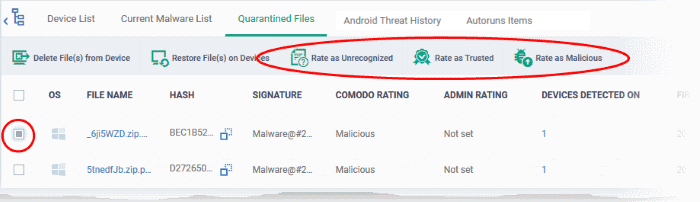
A confirmation will be displayed and the information will also be sent to the devices.
- Files rated as 'Malicious' will stay in quarantine on the device
- Files rated as 'Unrecognized' will be restored to their original locations on the device. Future AV scans may flag them as 'malicious' again
- Files rated as 'Trusted' will be restored to their original locations in the device. These files will be white-listed and skipped by future antivirus scans.
Export quarantined files records as a CSV file
- Click 'Security Sub-Systems' > 'Antivirus' > 'Quarantined Files' tab
- Click
the funnel
 icon to filter which records are included in the report.
icon to filter which records are included in the report.
- Click the 'Export' button and choose 'Export to CSV':
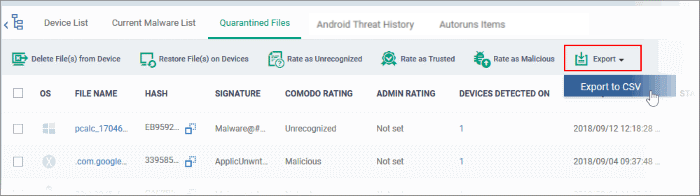
The report will be generated in .csv format.
The file will
be available in 'Dashboard' > 'Reports'. See Reports if you need more help with this interface.


