The Dashboard
- Click 'Dashboard' in the left menu to open this page.
The dashboard is divided into six sections:
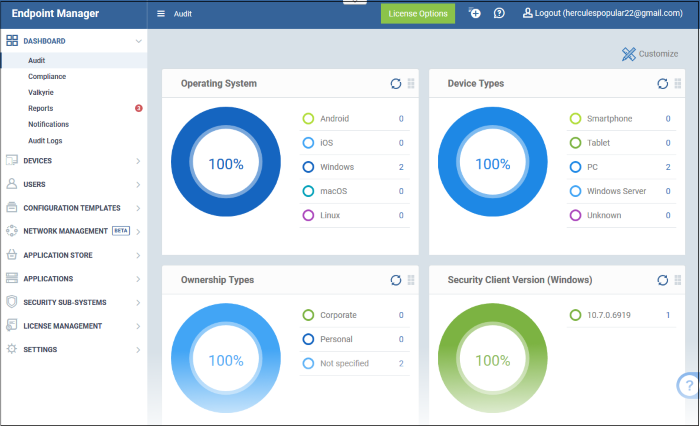
- Audit - Charts which show the operating systems and client versions installed on devices on your network. Also contains charts which show the types of devices in your network, and whether the devices are personal or corporate. See Audit section for more details.
- Compliance - Statistics which detail how compliant your devices are with EM security policies. For example, device connection status, devices with viruses, devices with blacklisted applications, rooted and jailbroken devices, and device scan status. See Compliance for more details.
- Valkyrie - A summary of verdicts on unknown files submitted to the Valkyrie file analysis system. See Valkyrie for more details.
- Reports - A list of all reports generated by Endpoint Manager. You can also create new reports from here. See Reports section for more information.
- Notifications - A list of notifications sent to the administrator by EM. See Notifications for more details.
-
Audit Logs - Displays a list of actions taken on managed devices by admins and staff. Example actions include applying profiles, remote installation of packages and more. See Audit Logs for more details.
- Click 'Dashboard' on the left then 'Audit'
- Click 'Customize' at top-right if you want to change which charts are shown on the page
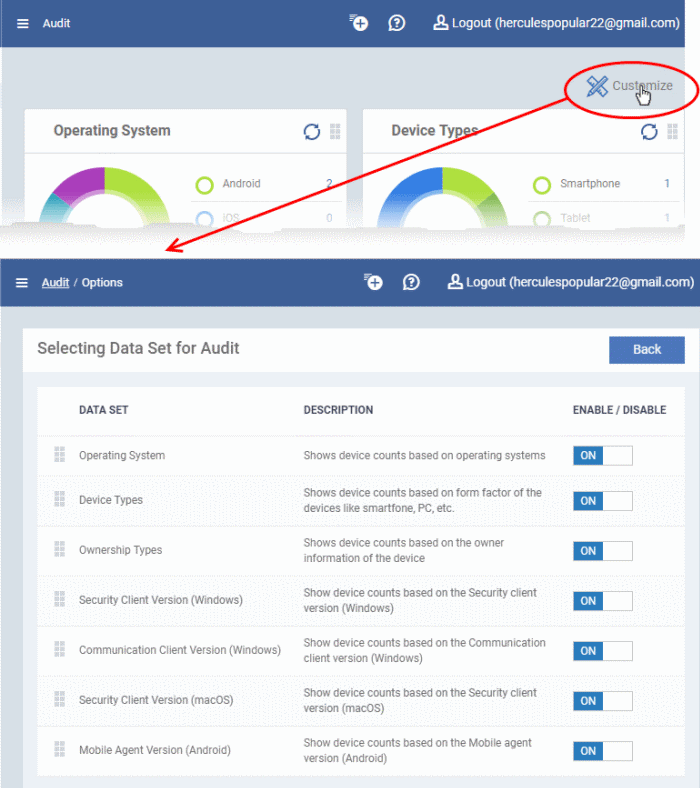
- Use the 'On/Off' switches to add or remove charts from the dashboard
- The 'Customize' icon
 shows the number of charts removed from the default view
shows the number of charts removed from the default view
- Click and hold the icon at top right of a tile to move it around the page
Operating System
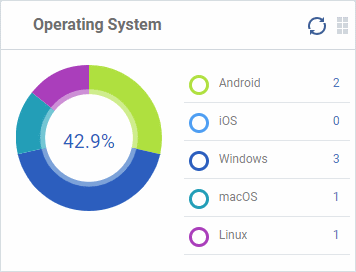
Shows enrolled devices by operating system. Place your mouse cursor over a sector or the legend to see further details.
- Click on an item in the legend
will open the respective 'Device List' page.
Security Client Version (Windows)
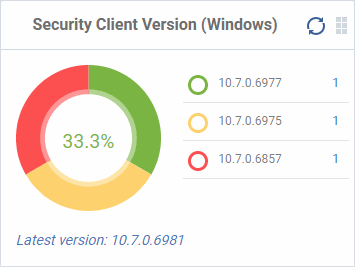
The versions of Comodo Client Security installed on Windows devices on your network. Comodo Client Security is the antivirus/security software on an endpoint.
- The number of devices using each version is shown to the right of the version number.
- Click the number to view all devices using that version.
- The latest version of the client is shown underneath the chart.
Update to the latest version - Click the number, select the target devices, then click 'Install or Manage Packages'.
See Remotely Install and Update Packages on Windows Devices for more details.
Communication Client Version (Windows)
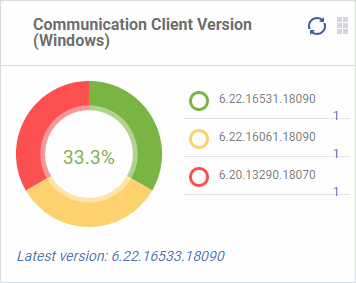
The versions of Communication Client installed on Windows devices on your network. This is the agent which sends updates to the EM console.
- The number of devices using each version is shown to the right of the version number.
- Click the number to view all devices using that version.
- The latest version of the client is shown underneath the chart.
- Update to the latest version - Click the number, select the target devices, then click 'Install or Manage Packages'.
Security Client Version (Mac OS)
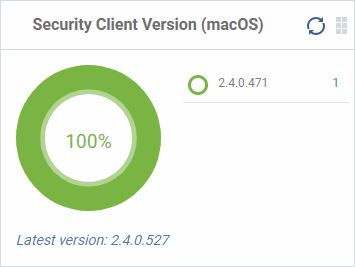
The versions of the security client installed on MAC OS devices on your network. The security client is the Comodo Client Security for MAC (CCS for Mac) software on an endpoint.
- The number of devices using each version is shown to the right of the version number.
- Click the number to view all devices using that version.
- The latest version of the client is shown underneath the chart.
See Remotely Install Packages on Mac OS Devices for more details.
Mobile Agent Version (Android)
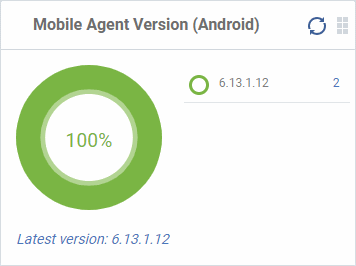
The versions of the mobile agent installed on Android device in your network.
- The number of devices using each version is shown to the right of the version number.
- Click the number to view all devices using that version.
- The latest version of the client is shown underneath the chart.
Device Types
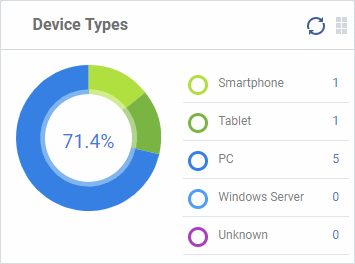
Shows the composition of your
device fleet by device type. Place your mouse cursor over a sector see further details.
- Click an item in the legend to view the respective 'Device List' page.
For example, clicking on 'Tablet' in the legend will open the 'Device List' page displaying the list of tablet devices. See 'Devices' for more details.
Ownership Types
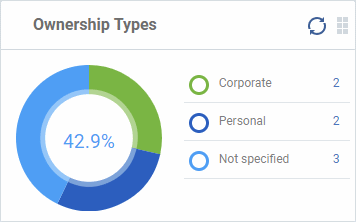
- Click an item in the legend to view the respective 'Device List' page
Change ownership type:
- Click 'Devices' > 'Device List' > click a device name > Click 'Owner' button > 'Change ownership'
The compliance dashboard monitors the status of managed devices with regards to various security and activity criteria. Charts shown include, devices with viruses, devices with blacklisted applications, device requiring database updates, rooted and jail-broken devices, devices which are unresponsive and more.
- To view the compliance status of devices, click 'Dashboard' in the left navigation then 'Compliance'.
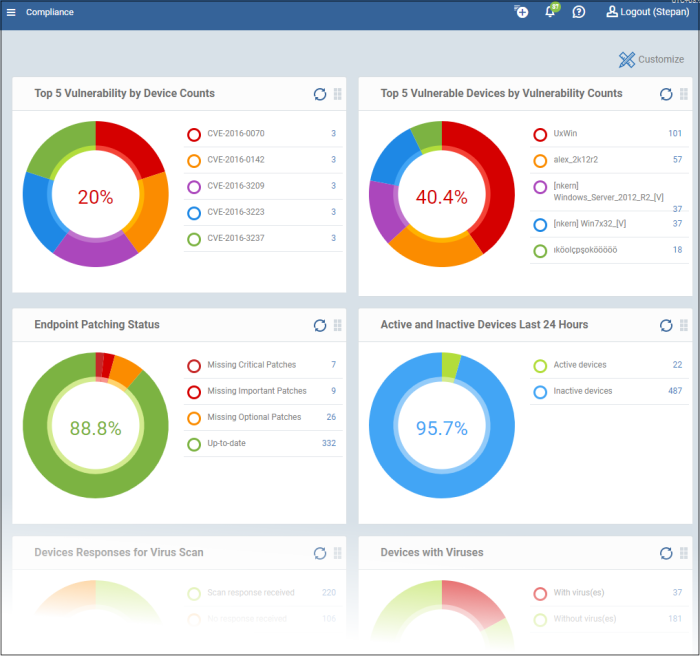
- To customize the charts shown in the interface, click the 'Customize' button
- To update the data in a tile, click the 'Refresh' icon at top right
- To move tiles around, click and hold the grid icon in the top right corner and drag the tile to the desired position.
Top 5 Vulnerability by Device Counts
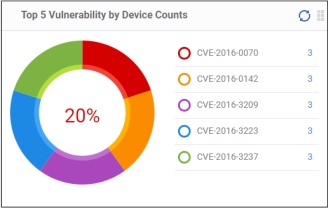
- Click
a vulnerability identifier (CVE code) to view the devices
that require the security patch. See 'Run
a Security Patch on Devices'
to know how to deploy the security patch.
Top 5 Vulnerable Devices by Vulnerability Counts
Shows the top five devices that require security patches. Placing the mouse cursor over a sector or the legend displays further details. See ‘Vulnerability Management’ for details about viewing vulnerabilities and running security patches on the devices.
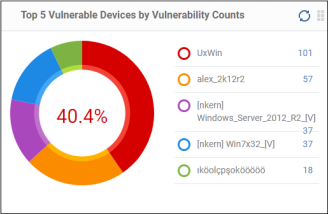
- Click
a
device name to view the details of the required patches.See
‘View
and Manage Patches for Windows and 3rd Party Applications’
for deploying patches on devices.
Endpoint Patching Status
Shows the patch statuses on your enrolled devices. Placing the mouse cursor over a sector or the legend displays further details. See Patch Management for details about deploying patches.
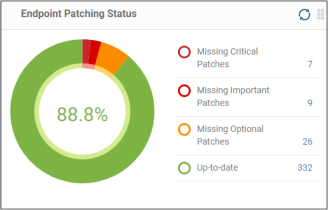
- Click an item in the legend to view the respective 'Device List' page.
For example, clicking ‘Missing Critical Patches’ will open the 'Device Management' page displaying devices that require the critical patches. See 'Devices and Device Groups' for more details.
Devices With Viruses
Shows how many enrolled devices are affected by viruses and how many are clean. Placing the mouse cursor over a sector or the legend displays further details. See Antivirus Scans for details about scanning for viruses on enrolled devices.
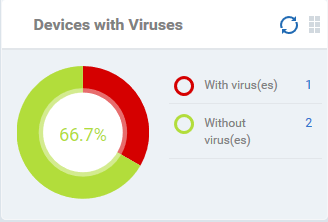
- Click an item in the legend to view the respective 'Device List' page.
Active and Inactive Devices Last 24 Hours
Shows the connectivity status of enrolled devices. Devices which have not contacted EM for more than 24 hours are marked as 'inactive'. Placing the mouse cursor over a sector or the legend displays the further details.
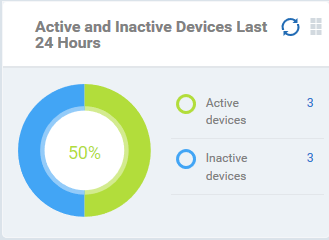
- Click an item in the legend to open the respective 'Device List' page.
Displays how many devices contain blacklisted apps versus those that are free of blacklisted apps. Placing the mouse cursor over a sector or the legend displays further details. See Applications for details about adding and removing apps from blacklist.
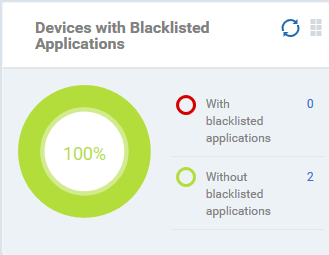
- Click an item in the legend to view the respective 'Device List' page.
Devices Responses for Virus Scan
Shows how many devices have responded to virus scan requests. Placing the mouse cursor over a sector or the legend displays the further details. See Antivirus Scans for details about scanning for viruses on enrolled devices.
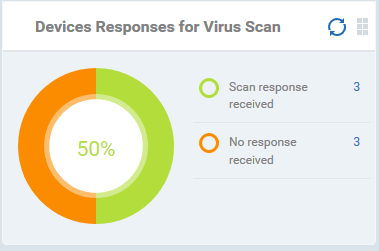
- Click an item in the legend to vie the respective 'Device List' page.
The 'Antivirus Device List' page allows you to run antivirus scans on selected devices. See Antivirus Scans for more details.
Rooted And Jail-broken Devices
Shows how many devices in your fleet are are rooted or jail-broken. Placing the mouse cursor over a sector or the legend displays the further details.
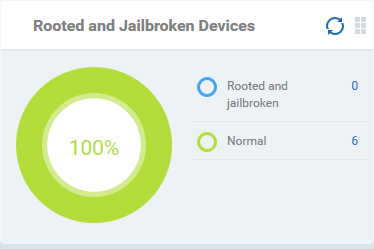
- Click an item in the legend to view the respective 'Device List' page.
Devices With Device Management Apps
Shows how many devices have the communication client. Android, Windows. Mac OS and Linux devices can only be enrolled with the EM app/communication Client (CC). iOS devices communicate with EM via the EM profile that was installed during enrollment and do not require the app. However, installing the app will provide enhanced functionality such as device location and the ability to send messages to the device from the admin panel.
Placing the mouse cursor over a sector or the legend displays the further details.
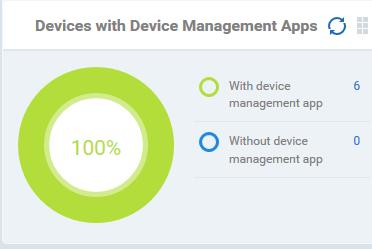
- Click an item in the legend to view the respective 'Device List' page.
For example,
clicking on 'With device management App' will open the 'Device List'
page displaying the list of devices that have the EM app installed. See 'Devices'
for more details.
Device Online
Shows enrolled devices by online/offline status. Devices will shown as offline if they are turned-off, are not communicating with EM for other reasons, or if Communication Client is not running. Placing the mouse cursor over a sector or the legend displays the further details.
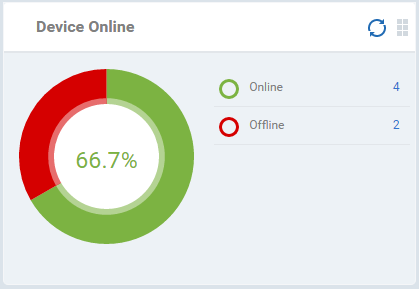
- Click an item in the legend to view the respective 'Device List' page.
For example, clicking on 'Online' will open the 'Device List' page displaying the list of devices that are online. See 'Devices' for more details.
Scan Status
Shows the progress and results of antivirus scans on enrolled devices. Placing the mouse cursor over a sector or the legend displays the further details.
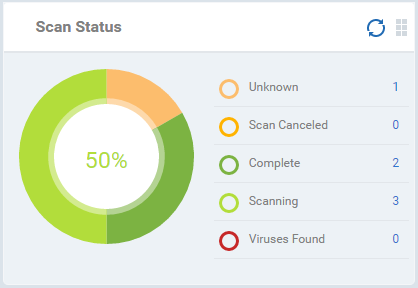
- Click an item in the legend to view the respective 'Device List' page.
For example, clicking on 'Virus Found' in
the legend will open the 'Antivirus Device List' page displaying the
list of devices in which the malware were detected. See 'Antivirus
Scans' for more details.
Antivirus DB Update
Shows the progress and results of AV database updates on enrolled devices. Placing the mouse cursor over a sector or the legend displays the further details.
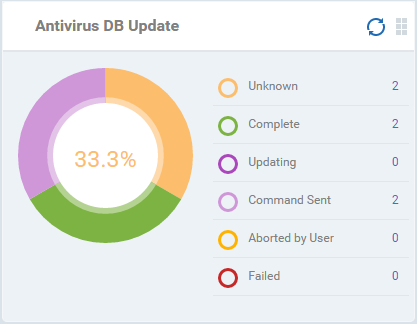
- Click an item in the legend to view the respective 'Device List' page.
For example, clicking on 'Complete' in the legend will show devices which have the latest virus database. See 'Antivirus Scans' for more details.
Security Product Configuration
Shows how many of your enrolled devices have 'Safe' or 'Not Protected' statuses. 'Not Protected' means:
- Comodo Client Security (CCS) is not installed on the devices
- CCS is installed but Anti-virus is not enabled in the deployed profiles on the devices
Placing the mouse cursor over a sector or on the respective legend displays the details.

- Click an item in the legend to view the respective 'Device List' page.
For example, clicking on 'Safe' will open the 'Device List' page displaying the list of devices that have Antivirus installed. See 'Devices' for more details.
- Valkyrie is a cloud-based file analysis service that tests unknown files with a range of static and behavioral checks in order to identify those that are malicious.
- To use the service, apply a profile to CCS that contains the 'Valkyrie' component.
- Click 'Configuration Templates' > 'Profiles'
- Click the name of the profile you want to edit, or click 'Create' to make a new profile
- Click the 'Add Profile Section' button > 'Valkyrie'
- Click 'Save'
- All results will be displayed in the Valkyrie dashboard. See Valkyrie Settings in Create
Windows Profile for more details.
|
Note: The version of Valkyrie that comes with the free version of EM is limited to the online testing service. The Premium/Managed version also includes manual file testing by ITarian research labs, helping enterprises quickly create definitive whitelists of trusted files. Valkyrie is also available as a standalone service. Contact your ITarian account manager for further details. |
Unparalleled Protection by
Comodo (Last Week)
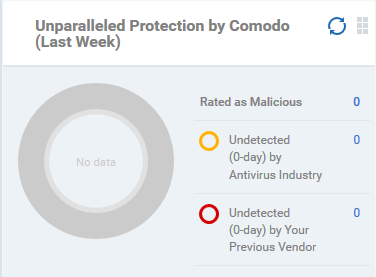
Shows the number of threats identified by Valkyrie over the past week versus the user's previous vendor and the antivirus industry as a whole.
Place the mouse cursor over a sector or the legend to see the percentage of number of files in a particular category.
See Manage File Trust Ratings on Windows Devices for more details on Windows File List screen.
Unparalleled Protection By Comodo (All Time)
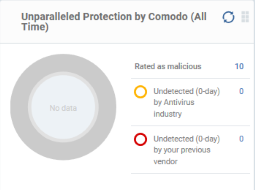
Shows the number of threats identified by Valkyrie since installation versus the user's previous vendor and the antivirus industry as a whole.
Place the mouse cursor over a sector or the legend to see the percentage of number of files in a particular category.
See Manage File Trust Ratings on Windows Devices for more details on Windows File List screen.
File Statistics (Windows Devices)
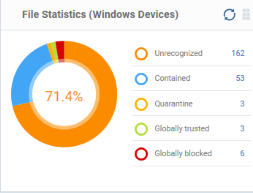
Shows the trust rating and status of files on your network.
See Manage File Trust Ratings on Windows Devicesfor more details on Windows File List screen.
- Click any item in the legend will to open the respective 'File List' page.
Valkyrie File Verdicts (Last Week)
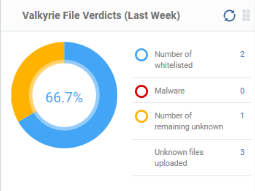
Displays Valkyrie trust verdicts on unknown files for the previous 7 days. This includes the number of unknown files identified as malicious, those that remain unknown, and those that were white-listed (trusted). The total amount of unknown files analyzed is shown at the bottom.
Place your mouse cursor over a sector or the legend to view the percentage of files in that category.
See Manage File Trust Ratings on Windows Devices for more details on Windows File List screen.
Valkyrie File Verdicts (All Time)
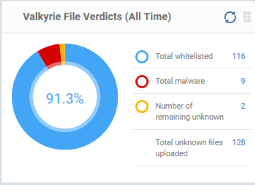
Displays Valkyrie trust verdicts on unknown files for the lifetime of your account. This includes the number of unknown files identified as malicious, those that remain unknown, and those that were white-listed (trusted). The total amount of unknown files analyzed is shown at the bottom.
Place your mouse cursor over a sector or the legend to view the percentage of files in that category.
See Manage File Trust Ratings on Windows Devices for more details on Windows File List screen.
Endpoint Manager can create a wide variety of reports on system and malware activity on your fleet of devices.
- Click 'Dashboard' on the left then 'Reports'
- The reports interface lets you generate and download many different report types:
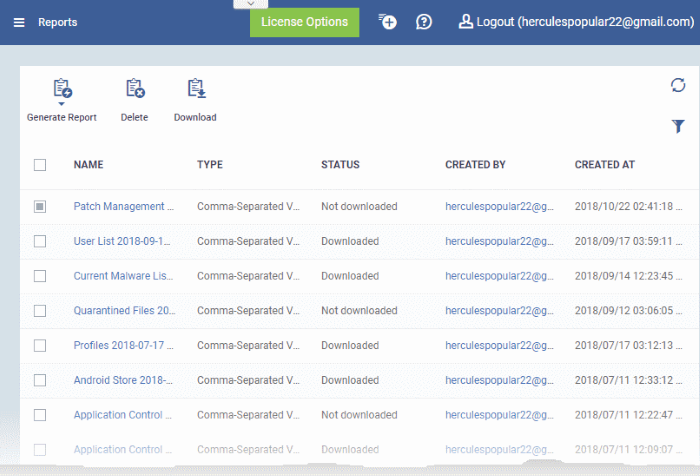
|
Column Header |
Description |
|---|---|
|
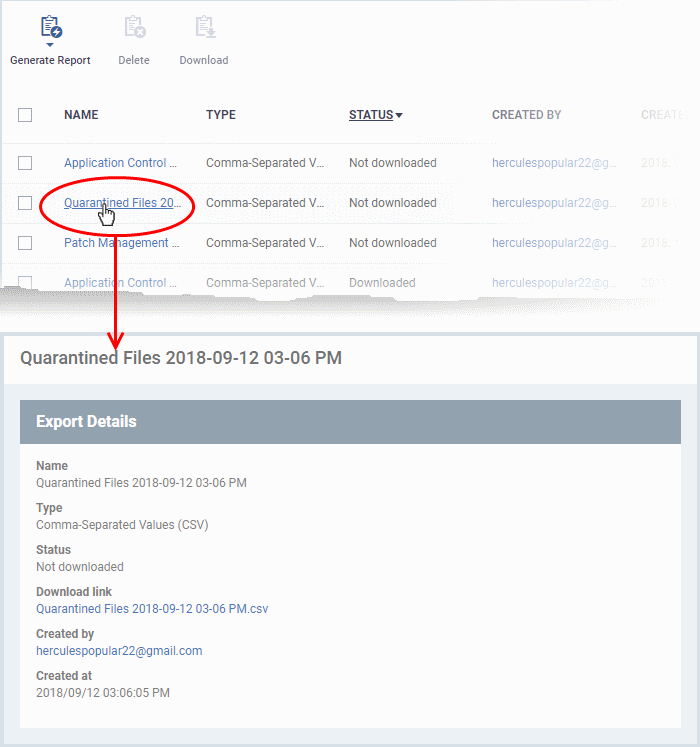
Name |
The subject of the report.
Click the name to view report details and download the report. |
|
Type |
The file format of the report. |
|
Status |
Whether or not the report has been downloaded by any user. |
|
Created By |
The admin who generated the report. Click the admin name to view their details. See View User Details if you need help with this. |
|
Created At |
The date and time the report was generated. |
- Click any column header to sort items in ascending/descending order of items in that column.
- Click the funnel icon at top-right to filter and search reports
You can generate reports from the reports interface or from individual product areas:
1. 'Dashboard' > 'Reports' interface - Lets you generate following report types:
- Android Antivirus
- Android MDM
- Windows Antivirus
- Windows Malware List
- Windows Top Malware
- Windows Quarantine
- Hardware Inventory
These reports are generated in spreadsheet (.xls) file format.
2. From specific interfaces:
- 'Users' menu
- User List - Click 'Users' > 'User Groups' > 'Export'. Click here for more details.
- User Groups - Click 'Users' > 'User List' > 'Export'. Click here for more details.
- Roles - Click 'Users' > 'Role Management' > 'Roles' > 'Export'. Click here for more details.
- Users - Click 'Users' > 'Role Management' > 'Users' > 'Export'. Click here for more details.
- 'Devices' main menu
- Device List – Click 'Devices' > 'Device List' > 'Export'. Click here for more details.
- Device Details > File List - Click 'Devices' > 'Device List' > Any Windows Device > 'File List' > 'Export'. Click here for more details.
- 'Configuration Templates' menu
- Profiles - Click 'Configuration Templates' > 'Profiles' > 'Export'. Click here for more details.
- Alerts - Click 'Configuration Templates' > 'Alerts' > 'Export'. Click here for more details.
- Procedures main menu
- Procedures List - Click 'Configuration Templates' > 'Procedures' > 'Export'. Click here for more details.
- Procedure Execution Logs - Click 'Configuration Templates' > 'Procedures' > 'any scrip procedure' > 'Execution Log' sub-tab > 'Export'. Click here for more details.
-
Network Management menu
- Discoveries - Click 'Network Management' > 'Discoveries' > 'Export'. Click here for more details.
- Managed Devices List - Click 'Network Management' > 'Devices' > ‘Managed Devices’ tab > 'Export'. Click here for more details.
- Discovered Devices List - Click 'Network Management' > 'Devices' > ‘Discovered Devices’ tab > 'Export'. Click here for more details.
- 'Application Store' menu
- iOS Store - Click 'Application Store' > 'iOS Store' > 'Export'. Click here for more details.
- Android Store - Click 'Application Store' > 'iOS Store' > 'Export'. Click here for more details.
- 'Applications' main menu
- Mobile Applications - Click 'Applications' > 'Mobile Applications' > 'Export'. Click here for more details.
- Patch Management - Click 'Applications' > 'Patch Management' > 'Operating System' tab > 'Export'. Click here for more details.
- 'Security Subsystems' main menu
- Containment – Click 'Security Sub-Systems' > 'Containment' > 'Export'. Click here for more details.
- Application Control - Click 'Security Sub-Systems' > 'Application Control' > 'Export'. Click here for more details.
Valkyrie - Click 'Security Sub-Systems' > 'Valkyrie' > 'Export'. Click here for more details.
- Device Control – Click 'Security Sub-Systems' > 'Device Control' > 'Export'. Click here for more details.
- Device List - Click 'Security Sub-Systems' > 'Antivirus' > 'Device List' tab > 'Export'. Click here for more details.
- Current Malware List - Click 'Security Sub-Systems' > 'Antivirus' > 'Current Malware List' tab > 'Export'. Click here for more details.
- Quarantined Files - Click 'Security Sub-Systems' > 'Antivirus' > 'Quarantined Files' tab > 'Export'. Click here for more details.
- Threat Android History - Click 'Security Sub-Systems' > 'Antivirus' > 'Android Threat History' tab. Click here for more details.
- Autoruns Items - Click 'Security Sub-Systems' > 'Antivirus' > 'Autoruns Items' tab > 'Export'. Click here for more details.
Data Loss Prevention - Click 'Security Sub-Systems' > 'Data Loss Prevention' > 'Quarantined Files’ tab > 'Export'. Click here for more details.
- License Management menu
- Licenses - Click 'License Management' > 'License Management' > 'Licenses' tab > 'Export'. Click here for more details
- Customers - Click 'License Management' > 'License Management' > 'Licenses' tab > select a license > 'Details' > 'Customers' tab > 'Export'. Click here for more details
Generate a report from the 'Reports' interfaceThese reports are generated in comma separated values (.csv) format.
- Click 'Generate Report' from the top and then click on the report type from the drop-down.
A new report
will be generated for the selected report type.
- To download a report, select it and click 'Download' at the top
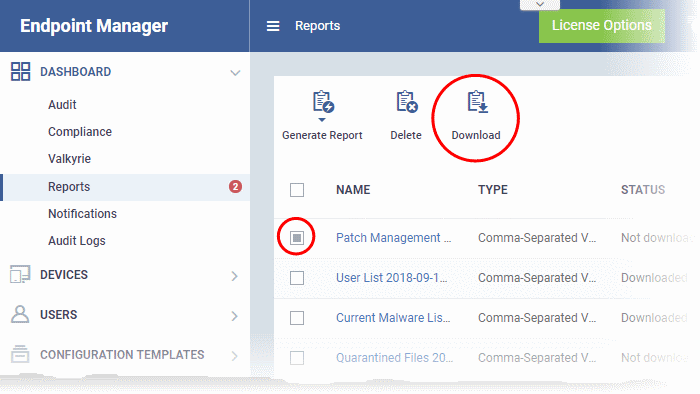
- To
remove a report from the list, select it and click 'Delete'.
- The
number of unread messages you have is shown on the notification
icon:

- Click
the icon to
view the messages.
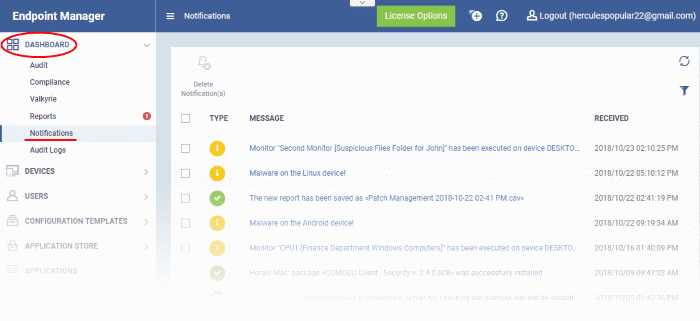
-
Message titles also act as shortcuts to the relevant interface. For example, clicking on 'Malware Found on Windows device' message opens the 'Antivirus Current Malware List' screen.
|
Tip: You can also receive notifications as emails. Click 'Settings' > 'Email Notifications' to configure them. See Configure Email Notifications if you need help with this. |
Audit Logs
- Click 'Dashboard' > 'Audit Logs'
- Endpoint Manager logs actions implemented on managed devices by admins and staff. These logs can be useful when troubleshooting issues.
- You can forward logs to an external syslog server if required. See Configure EM Audit Log Settings for more on this.
- Example logged actions include:
- Add or remove devices
- Apply a security profile
- Create or edit a profile
- Package installations
- Remote take-over sessions
- Changes to containment settings
- Remote file transfers
- Auto-removal of old / duplicate devices
- Each log entry is accompanied with details such as the staff member who applied the action, the affected device, the action taken, and more.
- Logs are kept for up to one year for PCI-DSS compliance.
- You can generate a report containing logs for the past three months as a comma separated values (CSV) file.
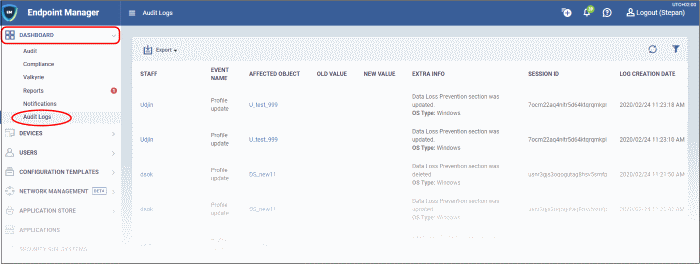
|
Audit Logs - Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
Staff |
Username of the admin or staff member who executed the action.
|
|
Event Name |
The action executed on the device. Examples include enrollment of devices, remote installation of Comodo and third party MSI packages, remote take-overs and device removals. |
|
Affected Object |
The device, device group, profile, procedure or file group on which the action was executed.
|
|
Old Value |
The previous setting or value before the action was implemented. For example, if a Comodo package is remotely updated, the old version number of the package will be shown here. |
|
New Value |
The new setting or value after the action was implemented. For example, if a Comodo package is remotely updated, the version number of the new package will be shown here. |
|
Extra Info |
Additional details about the action. Additional details include devices on which the procedure was run, package installation parameters, profiles applied/removed, malware quarantined, antivirus scans run and so on.
|
|
Session ID |
String used to identify the connection session between the device and the EM server during the action. |
|
Log Creation Date |
Date and time of the event. |
| Controls |
|
|---|---|
|
Export |
Generate a comma separated values (CSV) file of logs for a selected time period. The exported .csv is available in 'Dashboard' > 'Reports'. See Generate Audit Logs Reports for more details. |
- Click the 'Refresh' icon to load the latest events.
Search and filter options
- Click any column header (except 'Event Name') to sort items in alphabetical order of items in that column
- To
filter or search for a specific event, click the funnel icon at the
top right.
- You can filter items by various criteria or search for specific events.
- Click 'Apply' to run your filter.
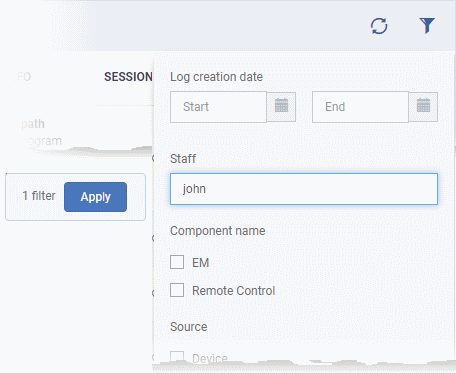
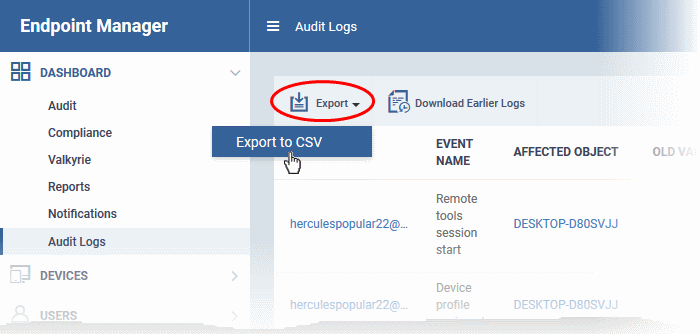
- Click 'Dashboard' > 'Audit Logs'
- Click
the funnel
 icon to filter which records are included in the report
icon to filter which records are included in the report
- Click 'Export' above the table then choose 'Export to CSV'. You can export logs for up to the past 90 days (Day 1 – Day 90)
- The CSV file will be available in 'Dashboard' > 'Reports'
- See Reports in The Dashboard for more details.


