Manage File Trust Ratings on Windows Devices
- Click 'Security ' > 'File Rating'
- Comodo Client Security (CCS) monitors all file activity on Windows devices. Every new executable is scanned against the Comodo white and blacklists then awarded a rating of 'Unrecognized', 'Trusted' or 'Malicious'.
- Files that have a rating of 'Unrecognized' or 'Malicious' are reported to the 'File Rating' interface. Admins can change the rating of a file as required.
- You can configure file analysis in the 'File Rating settings' section of the configuration profile applied to the device. See File Rating settings in the section Create a Windows Profile
- See File Ratings explained for background information on file ratings.
The File Rating Interface
The 'File Rating' interface lets you view the trust rating of files on an endpoint. Possible ratings are 'Unrecognized', 'Trusted' or 'Malicious', with 'Unrecognized' and 'Malicious' files being reported to this interface. You can manually set the rating of a file at your discretion.
- Files rated as 'Trusted' are allowed to run as normal on the endpoint.
- Files rated as 'Malicious' are quarantined and not allowed to run.
- Files rated as 'Unrecognized' are run inside the container - an isolated operating environment. Contained applications are not permitted to access files or user data on the host machine.
- You can also view a history of purged files. Purged files are those which existed on devices at one point in time, but are not currently present on any device.
- Apply
the 'Show Purged Files' filter to view these files. See the
explanation of Filter
Options given below.
- Click 'Security' > 'File Rating'
|
File Rating - Table of Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
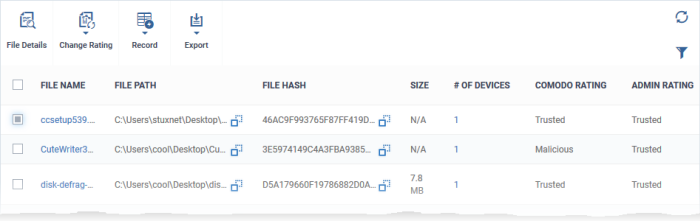
File Name |
The label of the application/executable file.
|
|
File Path |
The installation location of the application on the endpoint.
|
|
File Hash |
The SHA1 hash value of the executable file.
|
|
Size |
The size of the executable file. |
|
# of Devices |
The count of endpoints on which the item was found.
|
|
Comodo Rating |
The rating of the file as per the Comodo File Look-up service, reported by the CCS installations at the endpoints. See File Ratings Explained for more details. |
|
Admin Rating |
Indicates the rating of the file as manually set by the administrator, if any. |
Sorting,
Search and Filter Options
- Click any column header to sort items based in alphabetical order
- Click the funnel icon
 to open the filter options:
to open the filter options:
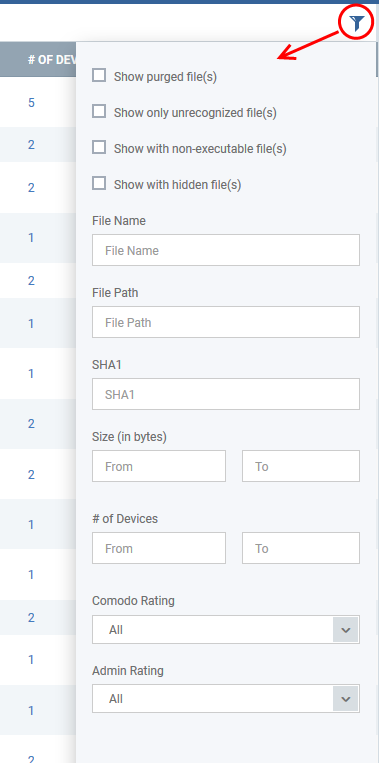
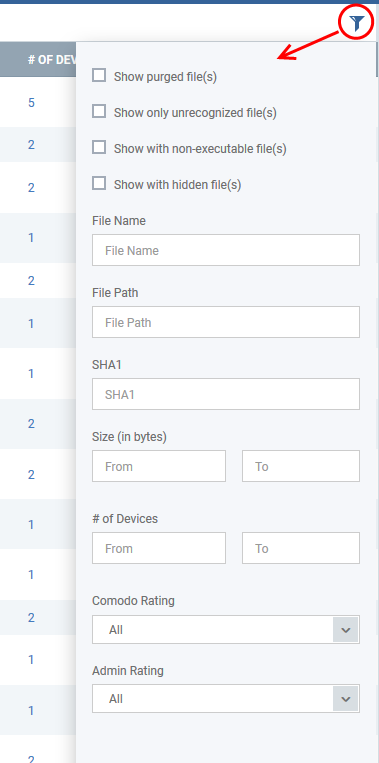
- Use the check-boxes to show or hide purged, non-executable, hidden or unrecognized files.
- Use the search fields to filter by file name, file path or SHA1 hash value. You can also filter by file size and the number of devices on which the file is present.
- Use the drop-down boxes to filter items by Comodo and/or Admin rating
- To display all items again, clear any search filters and click 'OK'.
You can use any combination of filters simultaneously to search for specific apps.
Manage File Rating
The File Rating interface
allows you to:
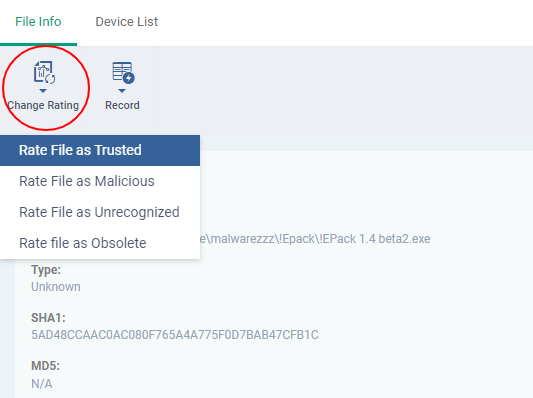
- Simply click on a file in the list or select a file and click 'File Details' at the top. The 'file info' screen shows basic file details and the devices on which the file is present. You can also change the trust rating of the file in this area.
- The file info screen shows file name, installation path, file type, version, size, hash values and the date the file was first encountered. The screen also shows the file's trust rating and the number of endpoints on which the file is present.
- The 'Change Rating' button allows you to manually set the file's rating as 'Trusted', 'Malicious' or 'Unrecognized':
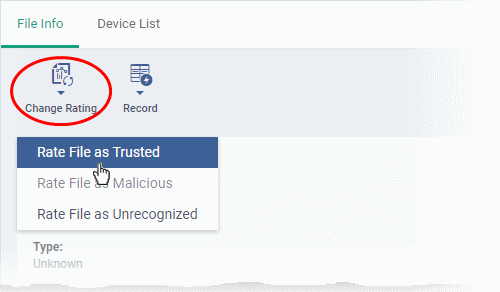
- The new rating will be sent to all endpoints.
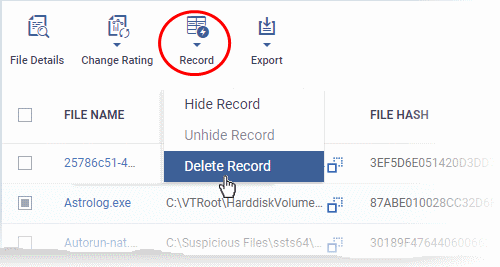
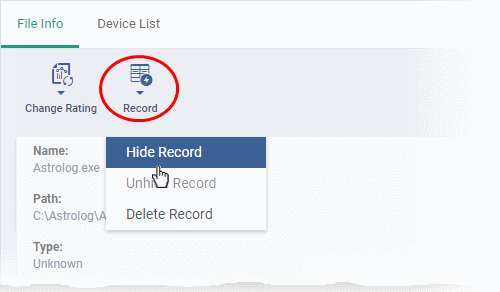
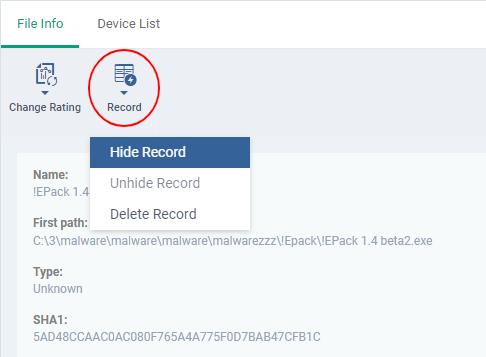
- The 'Record' button lets you hide, display or remove the file from the 'File Rating' list
- Click 'Security ' > 'File Rating' then click on a file in the list.
- Next, select the 'Device List' tab to see a list of all devices on which the file is present
- The 'Device List' Screen can also be opened by clicking on the number in the 'Number of Devices' column in the 'File Rating' table.
- The device list screen shows each endpoint on which the item was discovered. The screen also shows the installation path, the installation date and the file rating assigned by Comodo Client Security. The Viruscope column shows detailed info on processes started by the file.
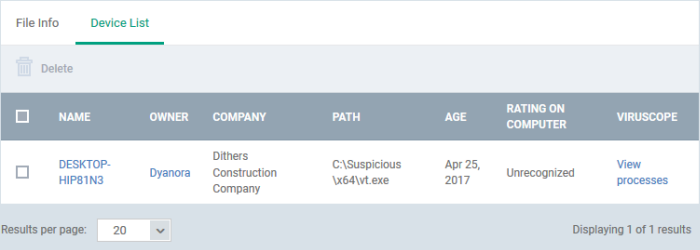
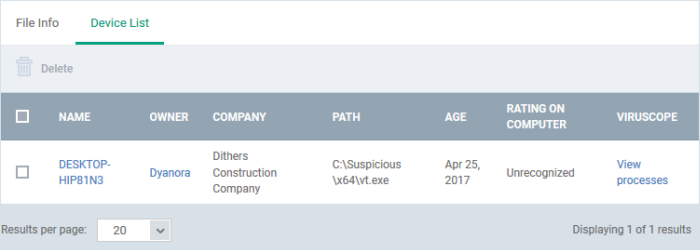
- You can remove the file from device(s) by selecting a device then clicking 'Delete'
View Process Activities of a File
|
Note: In order to fetch process activity data, VirusScope should be enabled in the profile in effect on the endpoint. See VirusScope Settings in Create a Windows Profile for more details. |
View the activities of a file on an endpoint
- Open the 'Device List' screen by clicking the file name or the number in the 'Number of Devices' column
- Click the 'View Processes' link in the 'Activity' column in the row of the device name.
- This will open a list of processes executed by the file on the selected endpoint:
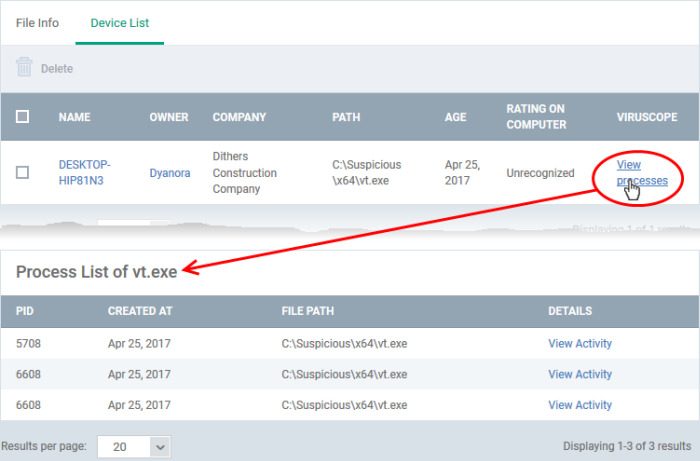
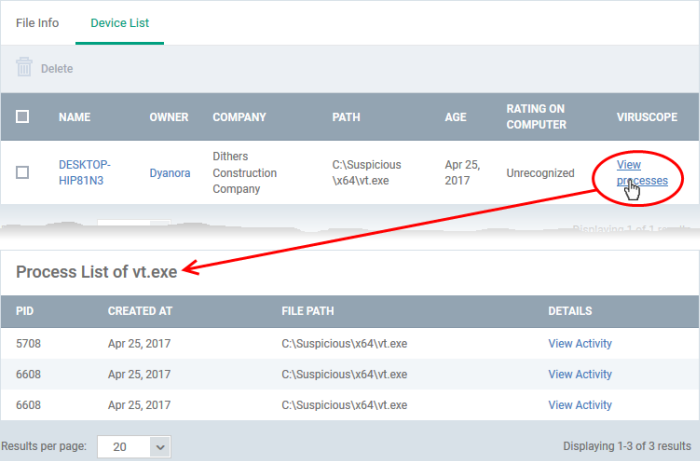
- Click 'View Activity' to see detailed information about each process. The 'Process Activity' interface has two tabs:
- Summary - Displays the name of the device and the installation path of the executable
- Activity - Displays a chronological list of activities by the selected process, including details of files modified by the process.
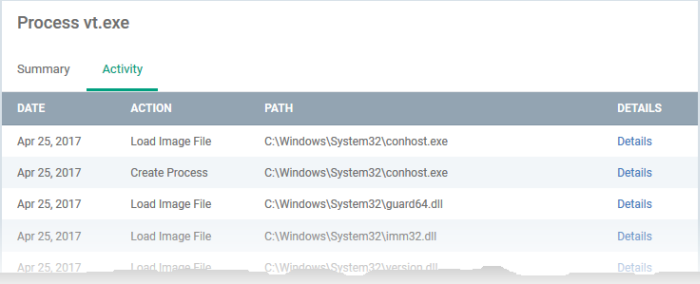
|
The 'Activity' - Table of Column Descriptions |
|
|---|---|
|
Column Heading |
Description |
|
Date |
Indicates the date and time of process execution. |
|
Action |
Indicates the action executed by the process on the target file. |
|
Path |
Indicates the path of the target file. |
|
Details |
Contains a link to view details of the action. |
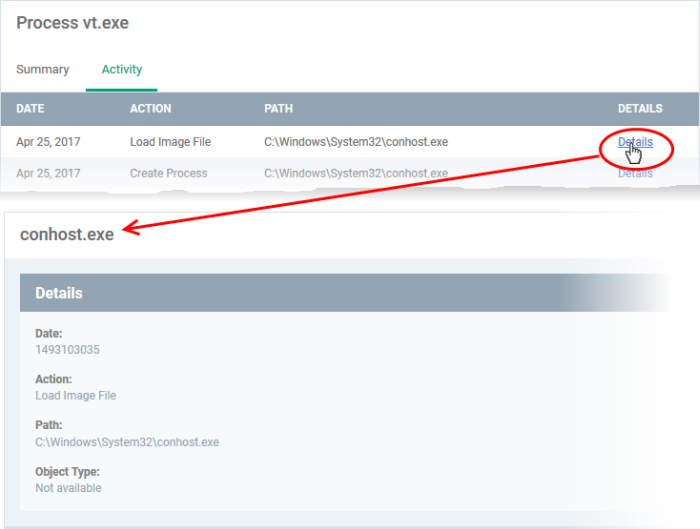
- You can inspect a particular activity by clicking the 'Details' link:
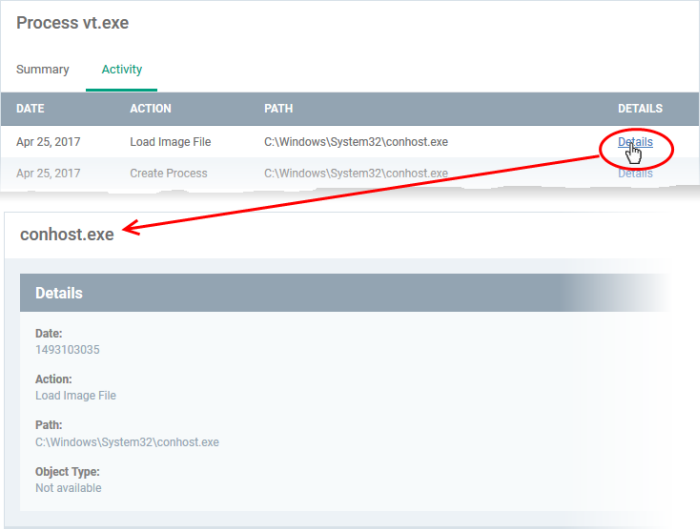
- Each file on an endpoint is automatically scanned and assigned a trust rating by Comodo Client Security on the endpoint.
- These ratings can be either 'Unrecognized', 'Trusted' or 'Malicious'. The rating for each file is shown in the 'Comodo Rating' column of the 'File Rating' interface.
- The file rating determines whether or how the file is allowed to run:
- Trusted – The file will be allowed to run normally. It will, of course, still be subject to the standard protection mechanisms of Comodo Client Security (behavior monitoring, host intrusion prevention etc).
- Malicious – The file will not be allowed to run. It will be automatically quarantined or deleted depending on admin preferences.
- Unknown – The file will be run inside the container. The container is a virtual operating environment which is isolated from the rest of the endpoint. Files in the container write to a virtual file system, use a virtual registry and cannot access user or operating system data.
- Automatic file rating can be configured in the 'File Rating' section of the configuration profile active on the endpoint. See File Rating settings in Create a Windows Profile for more details.
- Click 'Change Rating' in the 'File Rating' interface to manually set a rating for a selected file or files. The new rating will be propagated to all endpoints on which the item was identified and will determine the file's run-time privileges. Admin assigned ratings will be shown in the 'Admin Rating' column of the interface:
Assign a file rating to a file
- Select the file(s) whose rating you want to change and click 'Change Rating' button.
- Choose the rating you want to from the drop-down:
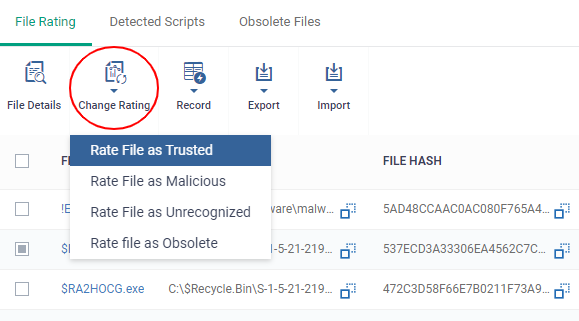
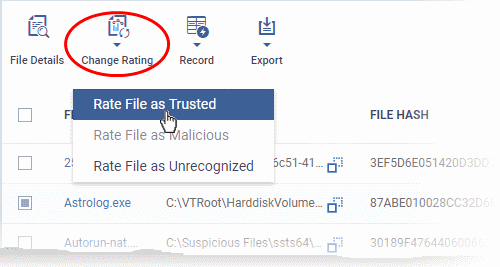
As mentioned, the admin rating will be set and sent to all endpoints. The admin rating will determine the file's run-time privileges.
- Select the file(s) to be hidden and click 'Record' at the top
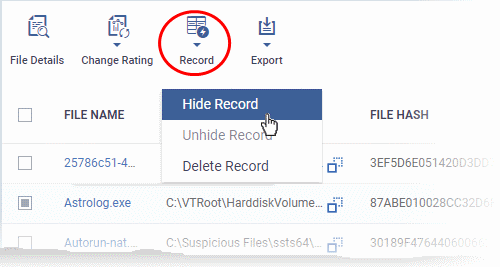
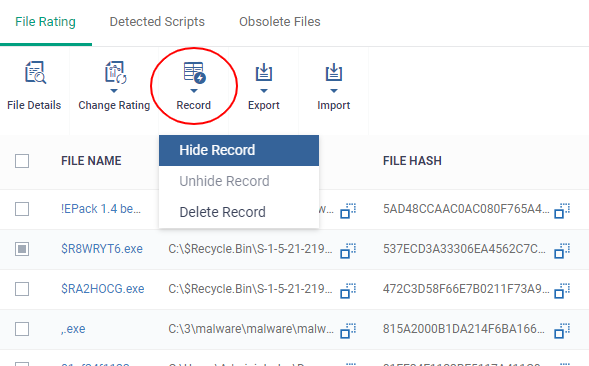
- Select 'Hide / Unhide / Delete Record' as required.
View hidden files
- Click the funnel icon at the top-right to open the filter options
- Select 'Show with hidden file(s)' and click 'Apply'
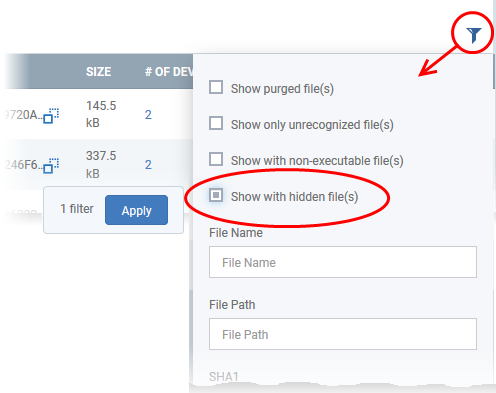
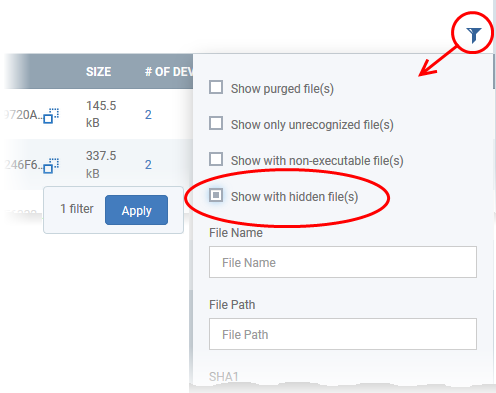
The hidden files will be included to the 'File Rating' interface. These files will be highlighted with a gray stripe.
Restore hidden files
- Click the funnel icon at the top-right to open the filter options
- Enable 'Show with hidden file(s)'
- Select the hidden files you want to restore click 'Record' and choose 'Unhide Record' from the drop-down
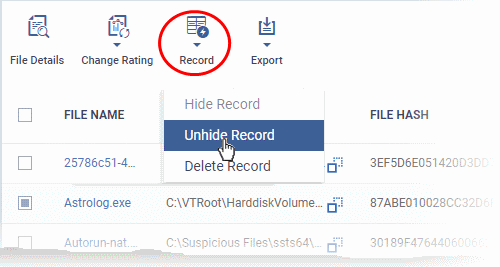
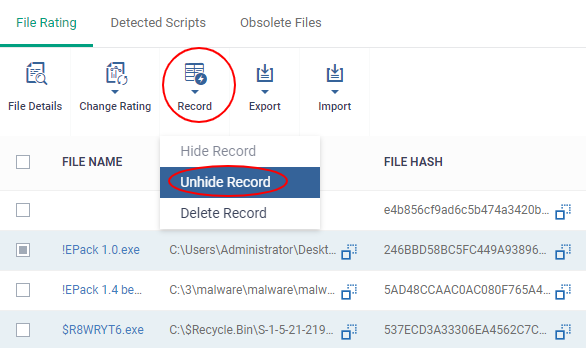
The files will be displayed in the list permanently.
Export a Report of the Files List
You can
export a file-rating report in .csv format as follows:
- Click 'Security' > 'File Rating'
- Click
the funnel
 icon to apply any filters you require
icon to apply any filters you require
- Click
the 'Export' button and choose 'Export to CSV':
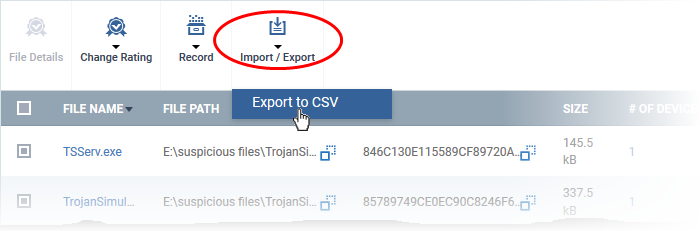
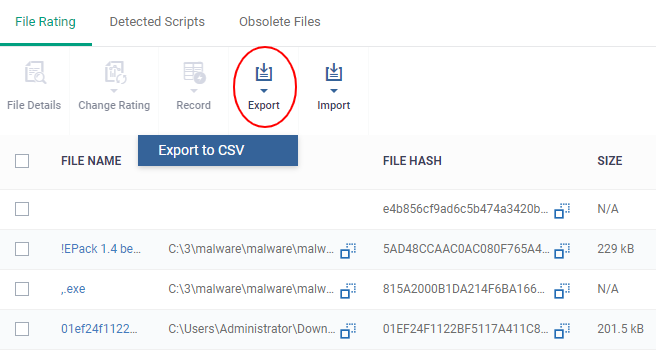
The report will be generated in .csv file format.
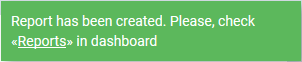
The report will be available in the 'Dashboard' > 'Reports' interface. See Reports if you need more help with this interface.
You can
hide files that you no longer wish to see in the list. The files will
be removed from the list but will not be deleted from the endpoints.
- Select the files you want to remove and click 'Record' at the top
- Choose 'Delete Record' from the drop-down
You can import a file to the file rating interface
- Click 'Security' > 'File Rating'
- Click the funnel
 icon to apply any filters you require
icon to apply any filters you require
- Click the 'Import' button and choose 'Import from CSV':

A pop up dialogue box will appear
- Click 'Choose File' to import your CSV file
- Select the file which you want to upload
- Click 'Import' to add your file to file rating

You will get a message that CSV file imported succesfully
Prequesties for importing a file
- The imported file must be in the proper format. In case of the following cases, "The CSV file is corrupt or not properly formatted." warning message will be displayed.
- Admin rating must be one of the following: "Trusted", "Unrecognized" or "Malicious"
- Hash and admin rating value should be added correctly or you will get "Missing/wrong typing of hash information" or "Missing/wrong typing of admin rating information" while uploading a file
- The files limit of maximum 1000 hashes can be added. When trying to import a file that exceeds the limit, the warning message "A maximum of 1000 hashes can be imported." will be displayed.