View Security Events by Time
- Click 'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select a company or group to view events in that group
Or
- Select 'Show all' to view all events
- Event view shows security events from all managed endpoints in chronological order:
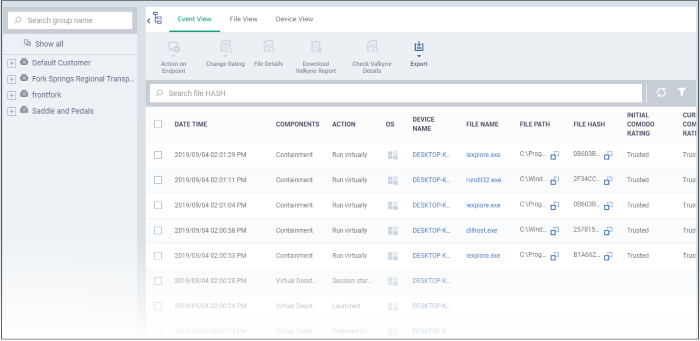
|
Security Dashboards – Event View – Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Date/Time |
The time at which the event occurred. |
|
Components |
The CCS module that reported the event. This can be 'Antivirus', 'Containment', 'Application Control', 'Autorun Control' or 'Virtual Desktop'. |
|
Action |
The response to the event.
This shows how the file was handled by the component mentioned above. Here are the possible actions per module: Antivirus – Windows, Mac OS, and Linux devices
Application Control - Windows devices
Autorun Control - Windows devices
Virtual Desktop - Windows devices
|
|
Device Name |
The label of the endpoint on which the event occurred.
|
|
File Name |
The label of the executable file affected by the action
|
|
File Path |
The installation location of the executable file on the endpoint.
|
|
File Hash |
The SHA 1 hash value of the executable file.
|
|
Initial Comodo Rating |
The trust rating awarded by Comodo File Look-up Service (FLS) to the file before the event. |
|
Current Comodo Rating |
The present trust rating of the file as per the Comodo FLS. |
|
Initial Admin Rating |
The trust rating of the file as manually set by the admin before the event, if any.
|
|
Current Admin Rating |
The most recent trust rating of the file as manually set by the admin after the event, if any.
|
|
Additional Info |
Provides the current status of the event or the action taken on the affected file. |
|
Controls |
|
|
Action on Endpoints |
Delete or restore a file from quarantine on the endpoint. Applies to events where malware or autorun items were quarantined.
|
|
Change rating |
Assign a new admin rating to a file (trusted, malicious or unrecognized).
|
|
File Details |
View complete information about the file that caused the event. You can also view a history of actions taken by the file.
|
|
Download Valkyrie Report |
Get a detailed Valkyrie analysis report for the file as a PDF. |
|
Check Valkyrie Details |
View the Valkyrie analysis on a file.
|
|
Export |
Save the list of events as a comma separated values (csv) file.
|
The 'Event View' interface lets you to:
Sorting, Search and Filter Options
- Click the 'Date/Time', 'File Name', 'File Path' or 'File Path' column header to sort events in ascending or descending order
- Enter the SHA 1 hash value of a file in the search box to filter the events involving the file.
- Click the funnel icon on the top right to open more filter options:
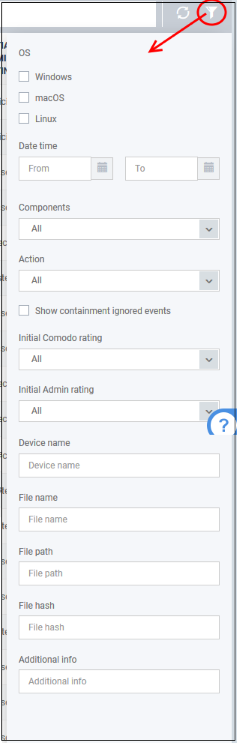
- Use the search fields to filter the events by OS, date/time, file ratings and other criteria.
- By default, 'Security Dashboards' > 'Event View' does not show the files that are ignored by auto-containment rules.
- Select 'Show containment ignored events' to include the files ignored by auto-containment rules in the events list
- To display all items again, clear any search filters then click 'OK'.
You can use any combination of filters simultaneously to search for specific apps.
You can delete or restore quarantined items from the 'Event View' tab of the security dashboard.
- Click 'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select a company or group to view events in that group
Or
- Select 'Show all' to view all events
- Select the events where the files of interest were moved to quarantine.
- Click 'Action on Endpoint' button:
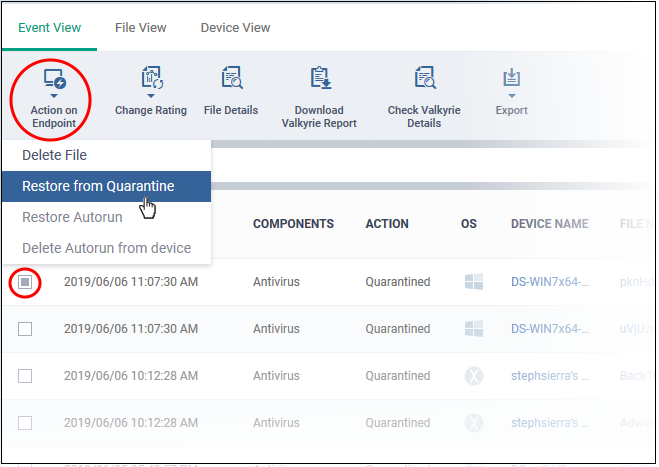
- Select 'Delete File / Delete Autorun from device' to remove the file from the device
- Select 'Restore from Quarantine' / 'Restore Autorun' to move the file(s) from quarantine to their original location on the device.
Rate Files as Trusted, Malicious or Unrecognized
If required, you can manually rate files as unrecognized, trusted or malicious. The new rating will be sent to endpoints during the next sync.
- Click
'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select a company or group to view events in that group
Or
- Select 'Show all' to view all events
- Select the events involving the files of interest.
- Click the 'Change Rating' button
- Set your preferred rating from the options:
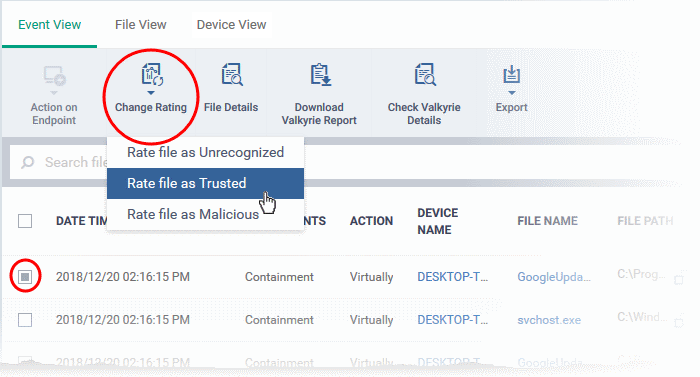
The new rating will be propagated to all endpoints during the next synchronization.
- You can view the complete details of the executable file that effected a security event on a managed endpoint from the 'Events View' interface.
- You can also view the history of actions taken on the file on all endpoints on which it was discovered.
View the details of a file that induced a security event
- Click
'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select a company or group to view events in that group
Or
- Select 'Show all' to view all events
- Select the event involving the file of interest.
- Click the 'File Details' button:
- Alternatively, click the label of the file in the 'File Name' column
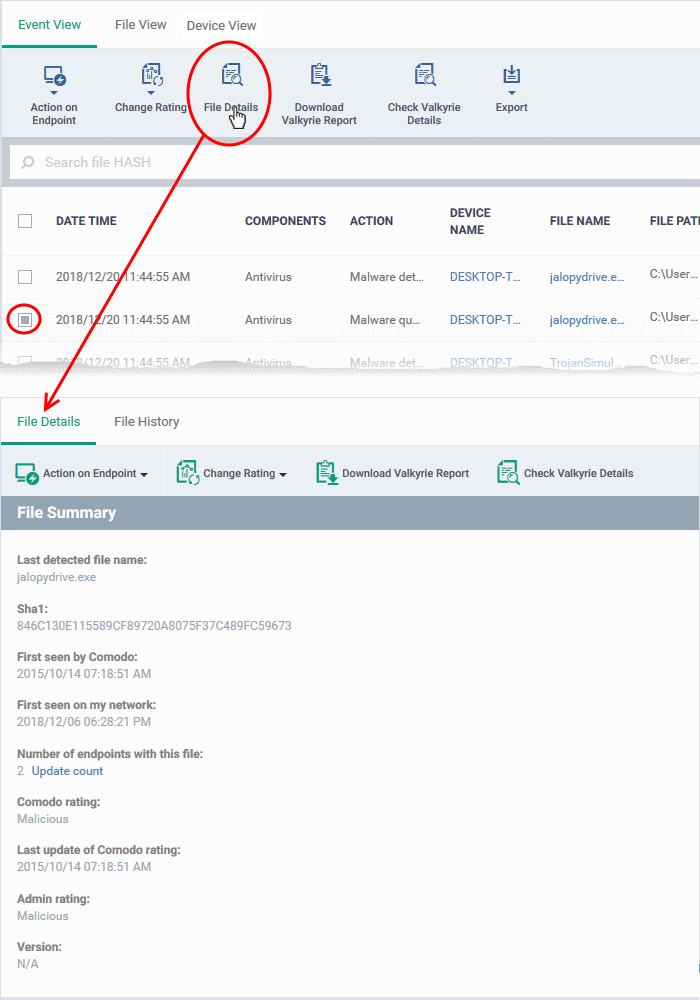
The information on the file are shown under two tabs:
- The 'File Details' tab shows the particulars of the file.
- The interface also allows you to:
- Change the admin trust rating of the file
- Delete the file from the endpoints or restore the file from quarantine, if the file has been moved to quarantine by antivirus on the endpoints.
- Get a Valkyrie analysis report of the file as a PDF
- View Valkyrie analysis details of the file
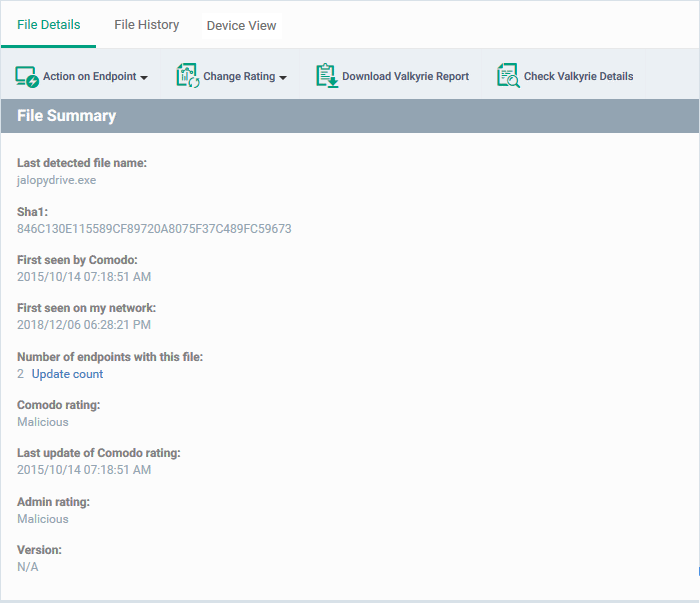
The 'File Summary' pane shows the following details:
Handle a quarantined file
- Last detected file name - Label of the file when it was most recently scanned
- SHA1 - SHA1 hash value of the file
- First Seen by Comodo - Date and time at which the file was first reported to Comodo threat labs
- First Seen on my Network - Date and time at which the file was first detected on one of your devices
- Number of endpoints - The count of Windows devices on which the file was found
- Click 'Calculate' to update the number of devices on which the file is currently found
- Comodo Rating - The trust verdict on the file from Comodo threat labs
- Last Update of Comodo Rating - Date and time at which the Comodo rating last changed
- Admin Rating - The trust rating most recently assigned to the file by an administrator, if any.
- Version - The version number of the executable file
- Click 'Action on Endpoint' on the top
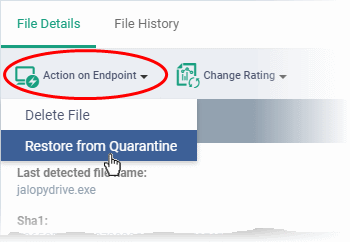
- Select 'Delete File' to remove the file the device, on which the selected event occurred.
- Select 'Restore from Quarantine' to move the file from quarantine to their original location on the device.
Assign or change the admin rating of the file
- Click 'Change Rating' on the top
- Set your preferred rating from the options:
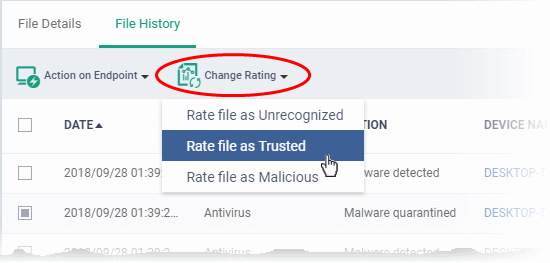
The new rating will be propagated to all endpoints during the next synchronization.
Download Valkyrie report of a file
- Click the 'Download Valkyrie Report' button
- See Get Valkyrie Report of a file for more details on the report
To view the Valkyrie analysis results of the file
- Click the 'Check Valkyrie Details' button
- See View Valkyrie analysis details of file for more details on the results
- This tab shows a timeline of events caused by the file. You can see the devices on which the file was found, the security module which detected the activity, and the action that was taken on the file
- The interface also allows you to:
- Change the admin trust rating of the file
- Delete the file from the endpoints or restore the file from quarantine, if the file has been moved to quarantine by antivirus on the endpoints.
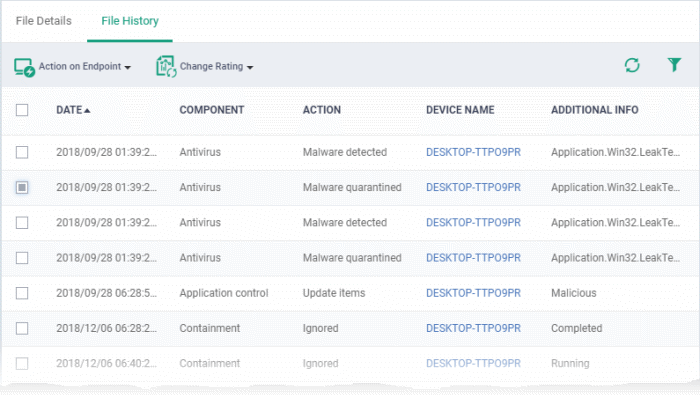
|
Security Dashboards - Event View - File History - Column Descriptions |
|
|---|---|
|
Column Header |
Description |
|
Date/Time |
The time at which the event occurred. |
|
Components |
The module that reported the event. This can be 'Antivirus', 'Containment', 'Application Control' or 'Autorun Control'. |
|
Action |
The nature of the event showing the how the file was handled by the CCS component. The possible actions are: Antivirus:
Containment
Application Control:
Autorun Control:
|
|
Device Name |
The label of the Windows endpoint on which the event occurred.
|
|
Additional Info |
Provides the current status of the event or the action taken on the affected file. |
|
Controls |
|
|
Action on Endpoints |
Allows you to delete a file or restore a file from quarantine on the endpoint. Applicable only for events involving 'Malware quarantined' action. |
|
Change rating |
Allows you to change the rating of the affected file to trusted, malicious or unrecognized. |
Handle a quarantined file
- Click 'Action on Endpoint' on the top
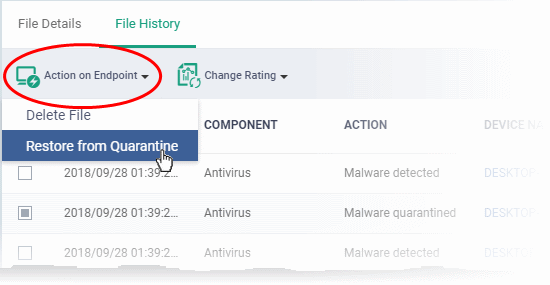
- Select 'Delete File' to remove the file the device, on which the selected event occurred.
- Select 'Restore from Quarantine' to move the file from quarantine to their original location on the device.
Assign or change the admin rating of the file
- Click 'Change Rating' on the top
- Set your preferred rating from the options:

The new rating will be propagated to all endpoints during the next synchronization.
Get the Valkyrie Report on a file
|
Background:
|
Download a Valkyrie report
- Click 'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select a company or group to view events in that group
Or
- Select 'Show all' to view all events
- Select the event involving the file of interest
- Click the 'Download Valkyrie Report' button
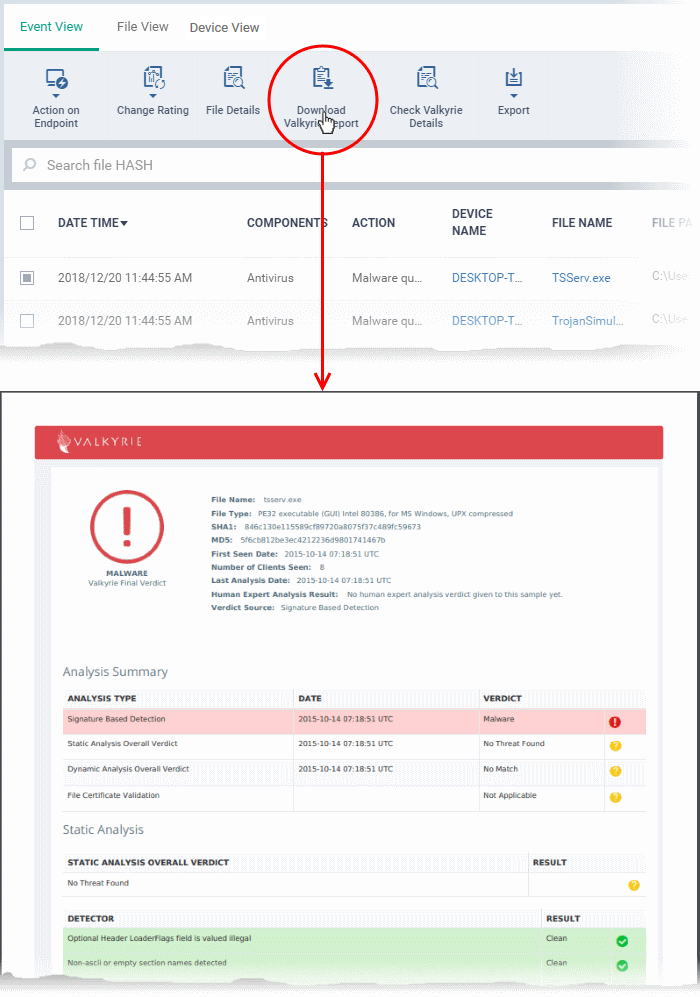
- The PDF opens in a new browser tab.
- The report contains granular details of various tests on the file
View Valkyrie analysis on a file
- Click 'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Select the event involving the file of interest.
- Click the 'Check Valkyrie Details' button
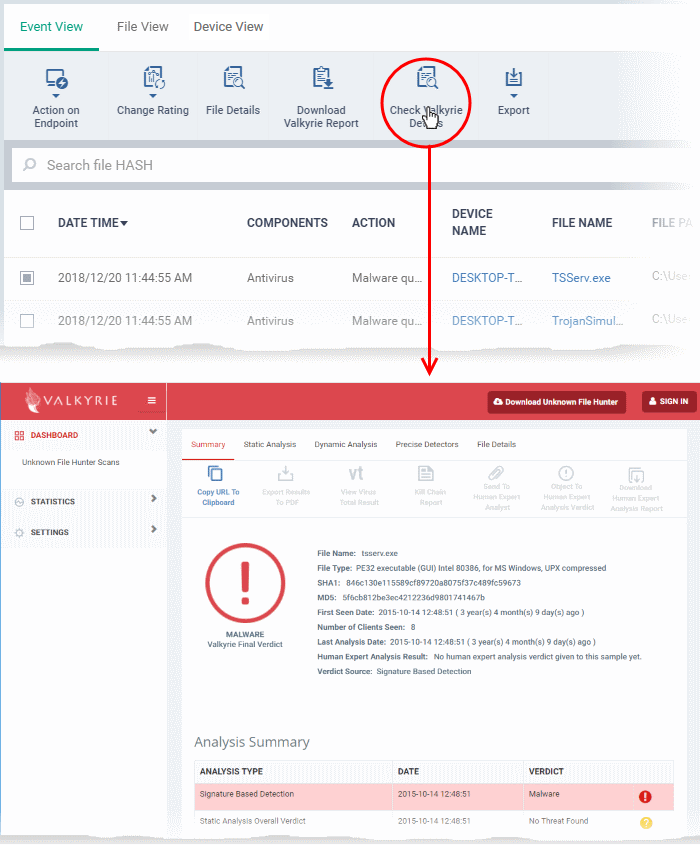
- The Valkyrie 'file verdict' page opens in a new tab.
- The page contains the results of various tests, and a trust verdict from each test.
- For more details on Valkyrie tests, see http://help.comodo.com/topic-397-1-773-9563-Introduction-to-Comodo-Valkyrie.html.
You can save the list of events as a comma separated values (CSV) file for future analysis.
- Click 'Security Sub-Systems' > 'Security Dashboards' > 'Event View'
- Apply any filters that you require.
- Click 'Export' > 'Export to CSV'
- The CSV file will be available in 'Dashboard' > 'Reports'
- See Reports in The Dashboard for more details.


